deviceTRUST Command Processor (dtcmd.exe)
The deviceTRUST Command Processor (dtcmd.exe) is used to interact with the deviceTRUST Host Service (dthost.exe) externally, or from within Custom Process tasks. It can be used to:
- Refresh the Microsoft AppLocker Policy.
- Query the properties of the current session.
- Import one or more policy files.
- Perform changes to the registry.
- Set the value of custom properties.
- Synchronize all properties.
- Trigger execution of a named sequence.
DTCMD.EXE is installed as part of the deviceTRUST Host software and resides within the installation path: %PROGRAMFILES%\DEVICETRUST\HOST\BIN and can be called without the path declaration.
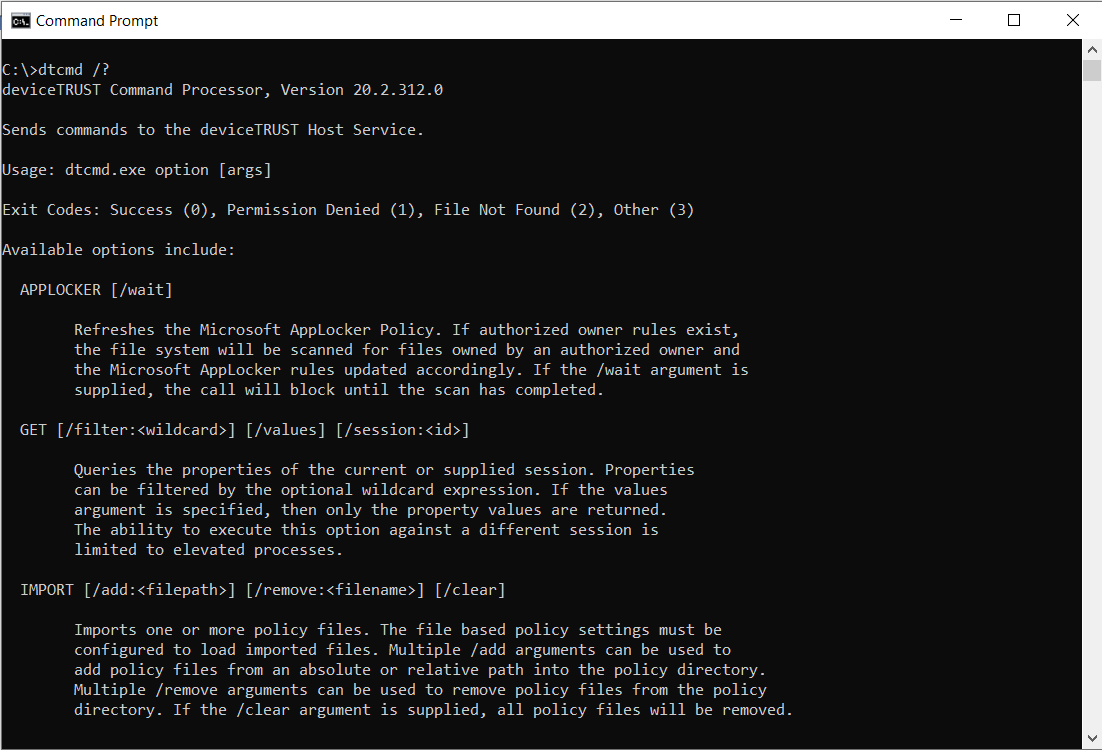
Option: APPLOCKER
Refreshes the Microsoft AppLocker Policy. If authorized owner rules exist, the file system will be scanned for files owned by an authorized owner and the Microsoft AppLocker rules updated accordingly. If the /wait argument is supplied, the call will block until the scan has completed.
APPLOCKER [/wait]
The APPLOCKER option can only be executed by users listed within the deviceTRUST Console under Settings -> Microsoft AppLocker Policy Settings -> Options -> External Refresh.
Option: GET
Queries the properties of the current or supplied session. Properties can be filtered by the optional wildcard expression. If the values argument is specified, then only the property values are returned. The ability to execute this option against a different session is limited to elevated processes.
GET [/filter:<wildcard>]
[/values]
[/session:<id>]
The ability to execute this option is configurable by policy. To enable the functionality, navigate to COMPUTER CONFIGURATION\ADMINISTRATIVE TEMPLATES\DEVICETRUST\SECURITY from a Local Policy or from a Microsoft Active Directory Group Policy and configure the ‘DEFINE WHETHER EXTERNAL PROCESSES CAN GET PROPERTIES OF THE USER’ policy.
Option: IMPORT
Imports one or more policy files. The file based policy settings must be configured to load imported files. Multiple /add arguments can be used to add policy files from an absolute or relative path into the policy directory. Multiple /remove arguments can be used to remove policy files from the policy directory. If the /clear argument is supplied, all policy files will be removed.
IMPORT [/add:<filepath>]
[/remove:<filename>]
[/clear]
The IMPORT option can only be executed by users listed within the deviceTRUST Console under Settings -> File-Based Policy Settings -> Load policy files imported by one of the following accounts.
Option: REG
Performs one or more changes within HKEY_CURRENT_USER or HKEY_LOCAL_MACHINE for the user identified by the session id. If no session id is specified, the current user is assumed. The changes are transactional therefore all succeed or all fail. A name can optionally be specified to undo the changes in a future call. One or more /update or /delete arguments must be specified. The update field takes the form Name;Value;Type;Subpath where Subpath can optionally extend the path argument, and type can be one of REG_DWORD, REG_SZ or REG_EXPAND_SZ. The delete field takes the form Name;Subpath where Subpath can optionally extend the path argument. The registry changes are reverted to their previous state when called with /undo, on disconnect when /persist is set to CONNECTION (the default), or on logoff when set to SESSION. When called with /protect, the path is secured to ensure that unprivileged users cannot modify the registry values. Undo operations do not impact security changes. The ability to execute this option is configurable by policy.
REG /path:<path>
[/name:<name>]
[/update:<update>]
[/delete:<delete>]
\[/persist:CONNECTION | SESSION | PERMANENT]
[/undo]
[/protect]
[/session:<id>]
The ability to execute this option is configurable by policy. To enable the functionality, navigate to COMPUTER CONFIGURATION\ADMINISTRATIVE TEMPLATES\DEVICETRUST\SECURITY from a Local Policy or from a Microsoft Active Directory Group Policy and configure the ‘DEFINE WHETHER EXTERNAL PROCESSES CAN CHANGE REGISTRY VALUES’ policy.
- To apply quotes within the [/update:<update>] argument, replace the quotes with the %QUOTE% variable.
Option: SET
Sets the values of one or more custom named properties. Properties must use the prefix ‘HOST_CUSTOM_’ and contain only uppercase alphanumeric characters or the underscore symbol. Multiple properties can be updated or deleted in a single command by specifying multiple /update or /delete arguments. If /hash is specified, then all supplied property values are set to a SHA256 hash of the supplied property value.
SET [/session:<id>]
[/update:<name>=<value>]
[/delete:<name>]
[/hash]
The ability to execute this option is configurable by policy. To enable the functionality, navigate to COMPUTER CONFIGURATION\ADMINISTRATIVE TEMPLATES\DEVICETRUST\SECURITY from a Local Policy or from a Microsoft Active Directory Group Policy and configure the ‘DEFINE WHETHER EXTERNAL PROCESSES CAN SET PROPERTIES OF THE USER’ policy.
Option: SYNC
Synchronises all properties, ensuring that all properties are available on the current or specified session, and optionally that the corresponding Logon or Reconnect triggers have been launched. An optional timeout in seconds can be supplied, which defaults to 30 seconds. The ability to execute this option against a different session is limited to privileged processes.
SYNC [/session:<id>]
[/timeout:<t>]
[/triggers]
Option: TRIGGER
Triggers the named sequence on demand. Each sequence with the given name found within the provided action name will be executed. If a named sequence has context filters then the sequence will only execute if all context filters match the current state of the session.
TRIGGER /action:<nameofaction>
/name:<nameofsequence>
[/session:<id>]
The ability to execute this option is configurable by policy. To enable the functionality, navigate to COMPUTER CONFIGURATION\ADMINISTRATIVE TEMPLATES\DEVICETRUST\SECURITY from a Local Policy or from a Microsoft Active Directory Group Policy and configure the ‘DEFINE WHETHER EXTERNAL PROCESSES CAN INVOKE NAMED TRIGGERS’ policy.
