deviceTRUST 19.4.100
This release includes new features and bug fixes to the deviceTRUST Host and Client for Microsoft Windows. For upgrading users, please refer to Policy Compatibility for important changes in this release.
New Send Mail task
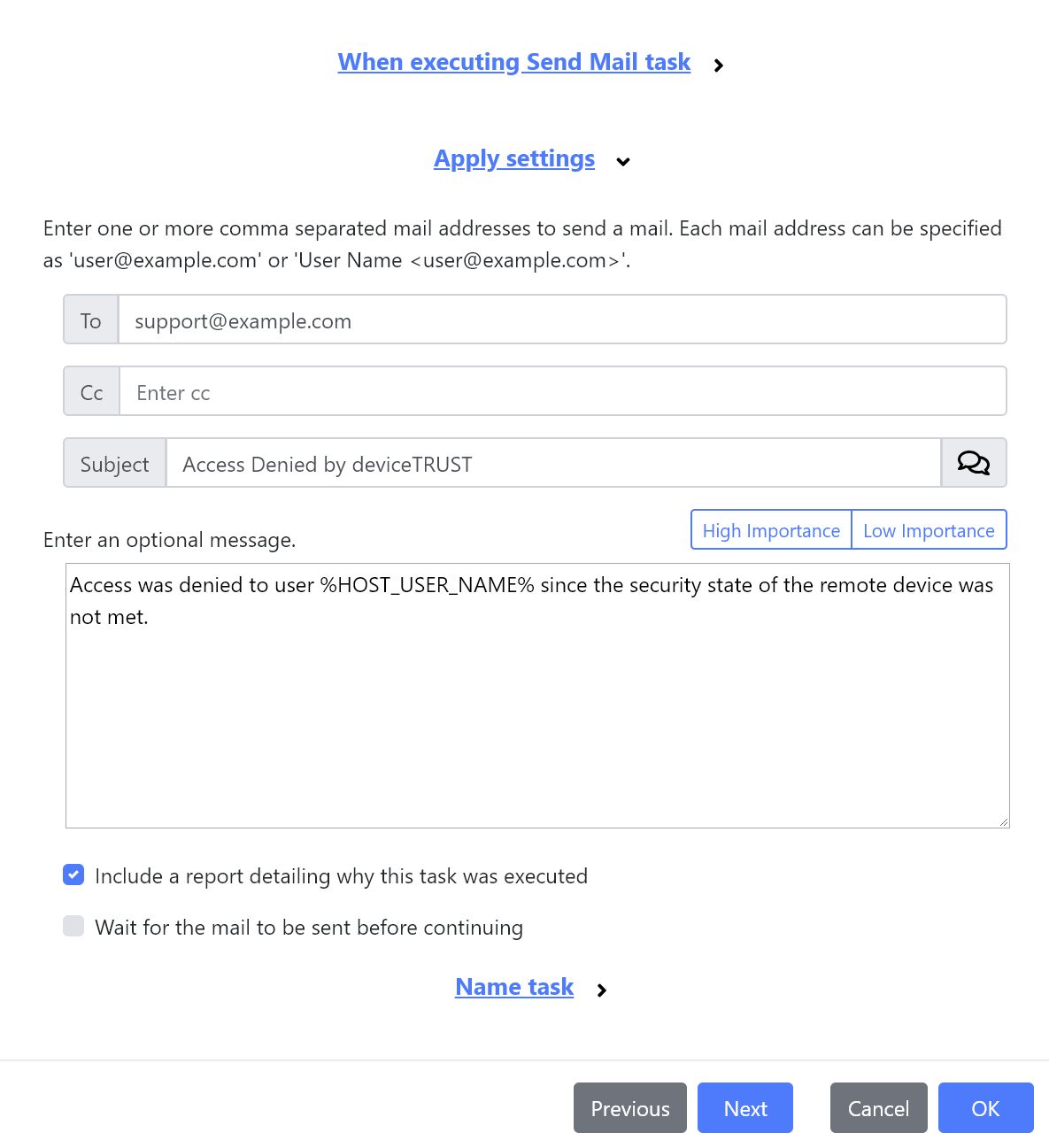
We’ve added a new Send Mail task that can be used to send an mail message. This can be useful for reporting additional details of why an action has occurred, such as a user being denied access to the shell. This works great with the new Named Triggers and Custom Buttons and Enhancements to Custom Process task, and can be used to minimise those users who are denied access to the shell.
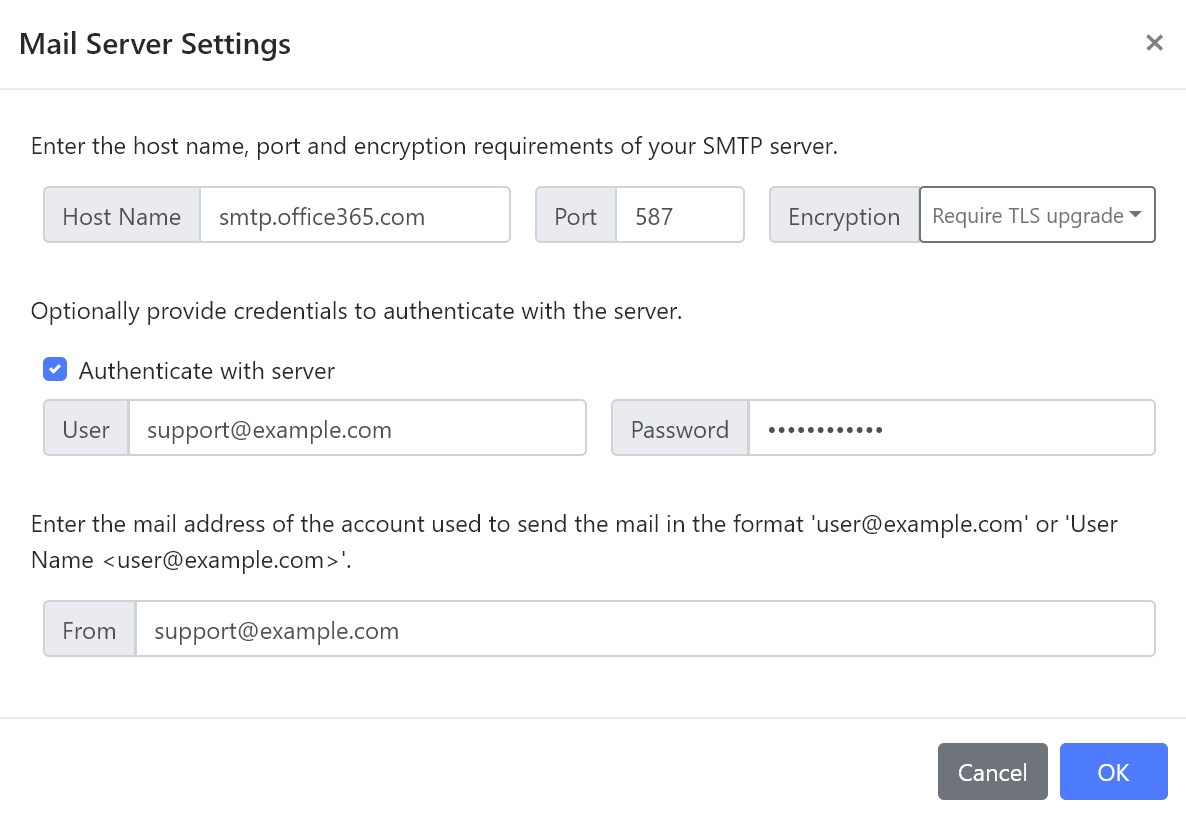
The Send Mail task relies upon a single definition of a Mail Server available within the new Settings tab.
The Send Mail task includes a checkbox Include a report detailing why this task was executed which when checked, appends a report to the mail message detailing the status of the endpoint, why the task was executed and why the context is set to its current value:

New Web Request task
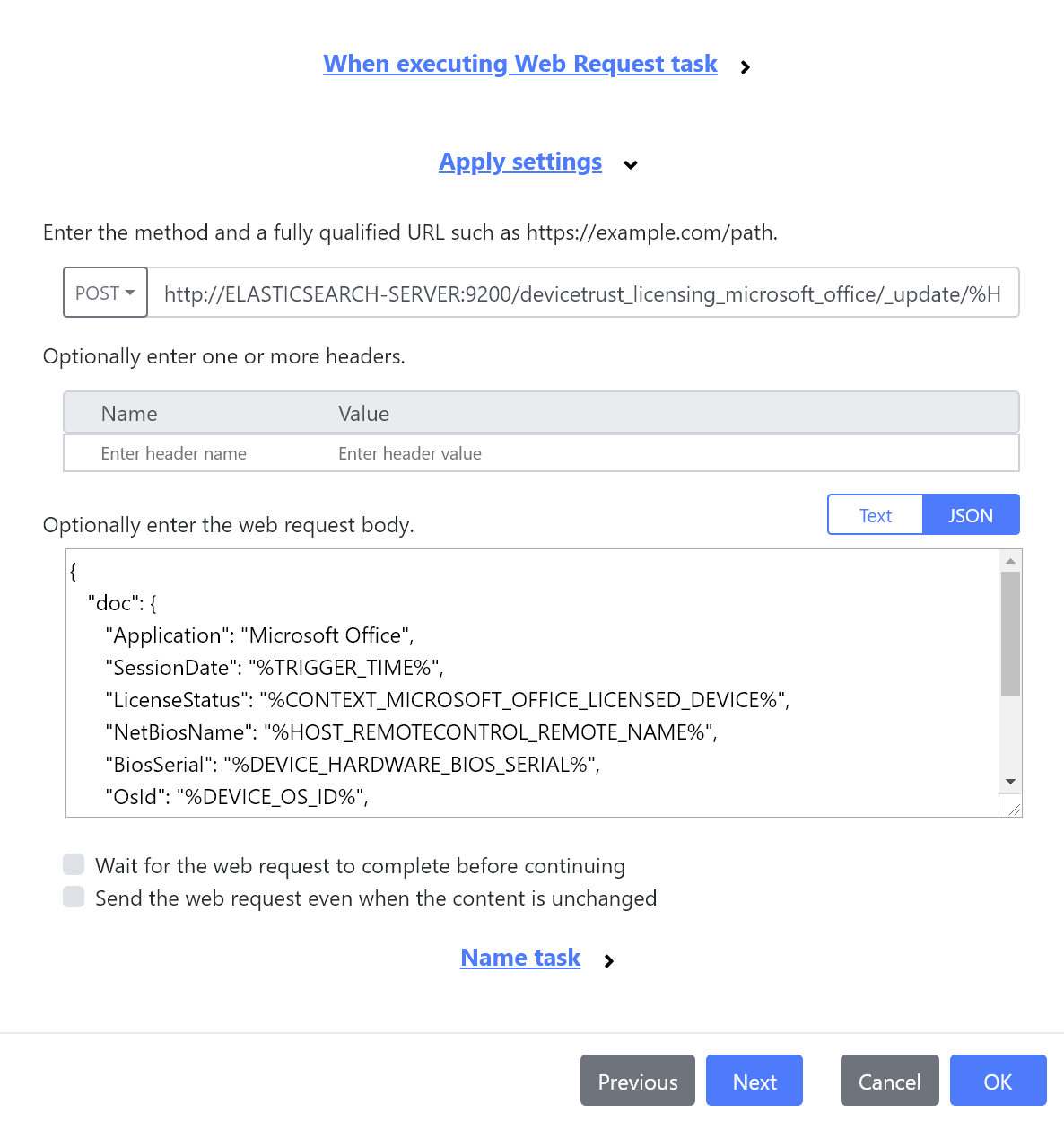
The new Web Request task allows a HTTP request to be made to a specified URL. This can be used to send data to web servers, for example to produce reports detailing the status of endpoints.
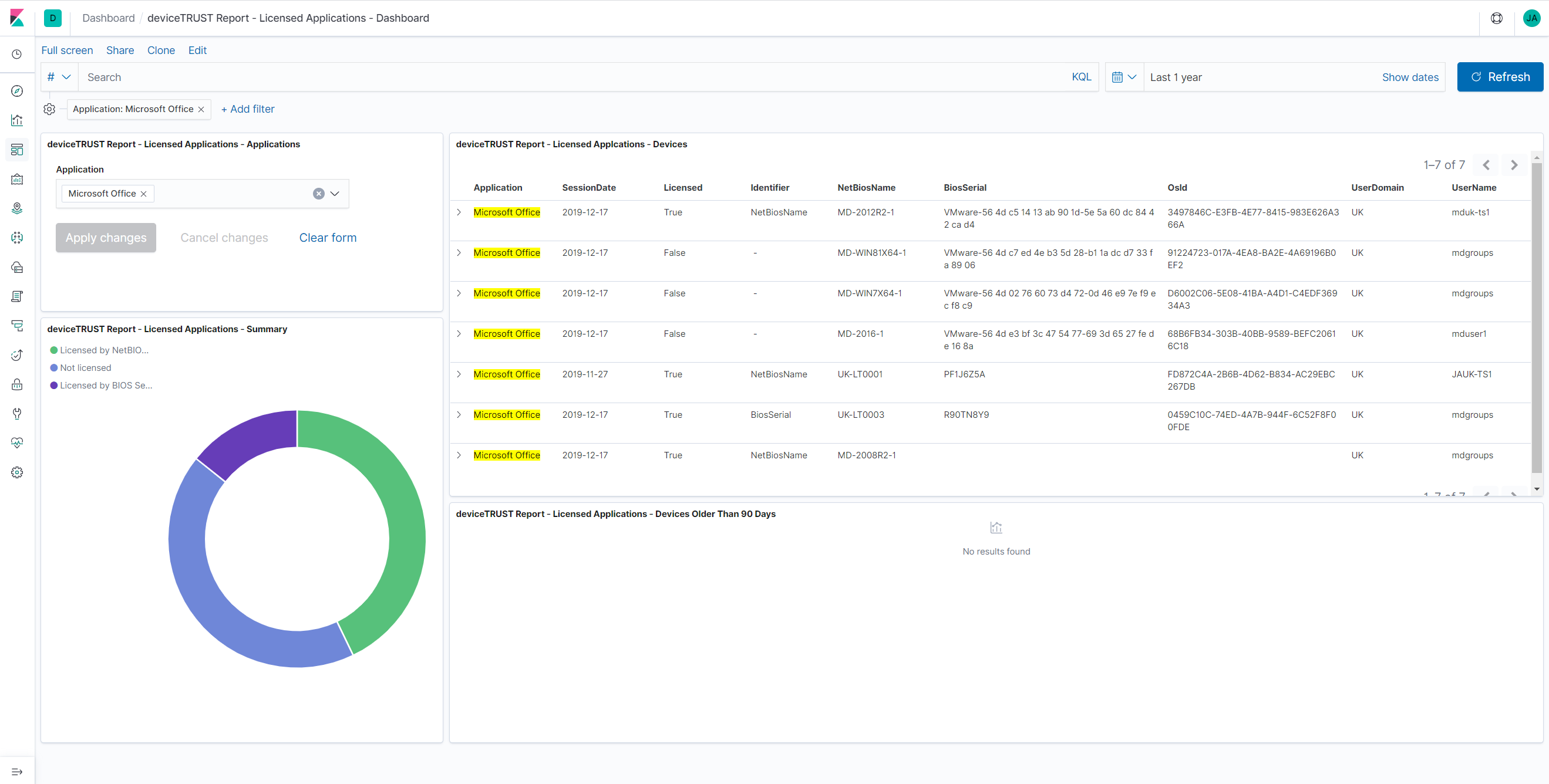
Elasticsearch Licensed Applications report
We’ve included a set of Elasticsearch reports for reporting on licensed applications. These include out of the box templates for reporting on Microsoft Office, Visio and Project, however can be easily extended to other licensed applications. A new guide is available titled Licensed Application Reporting which details how to import and configure the report within an existing Elasticsearch instance.
Enhancements to Custom Process task
You can now choose whether the Custom Process task should be executed locally on the host, or remotely on the client.
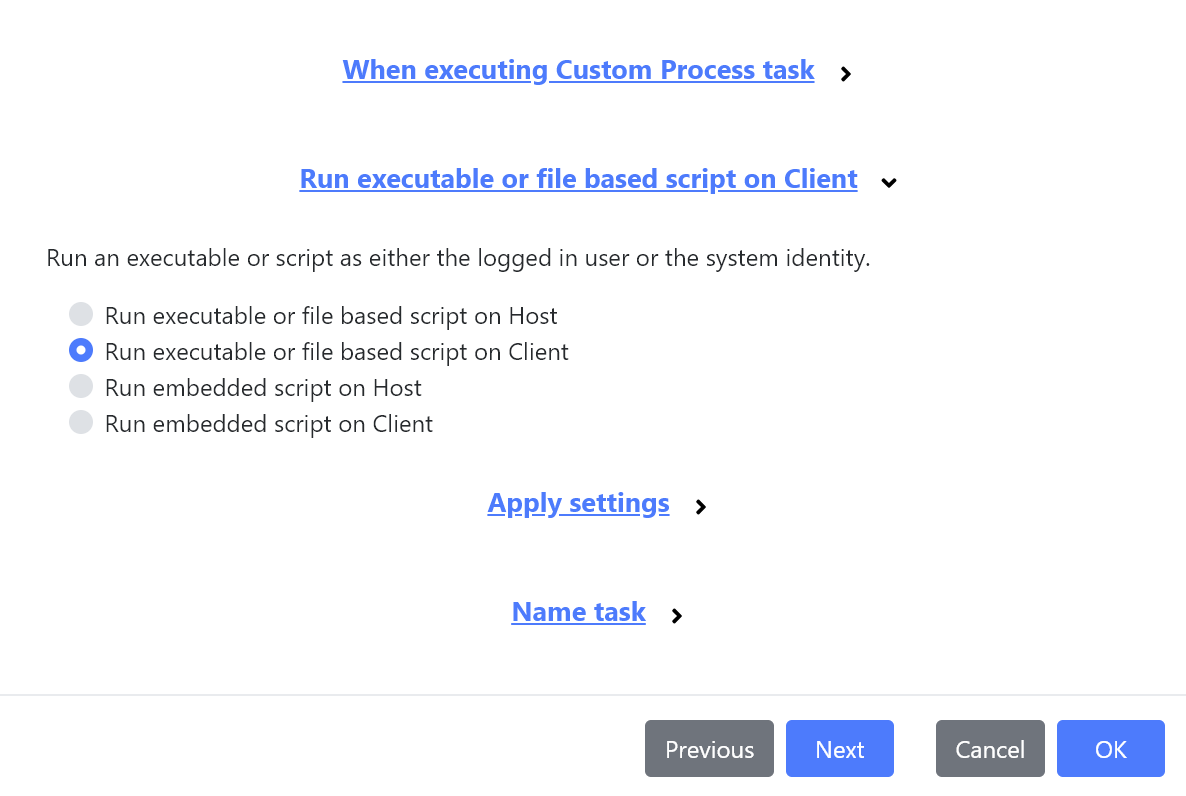
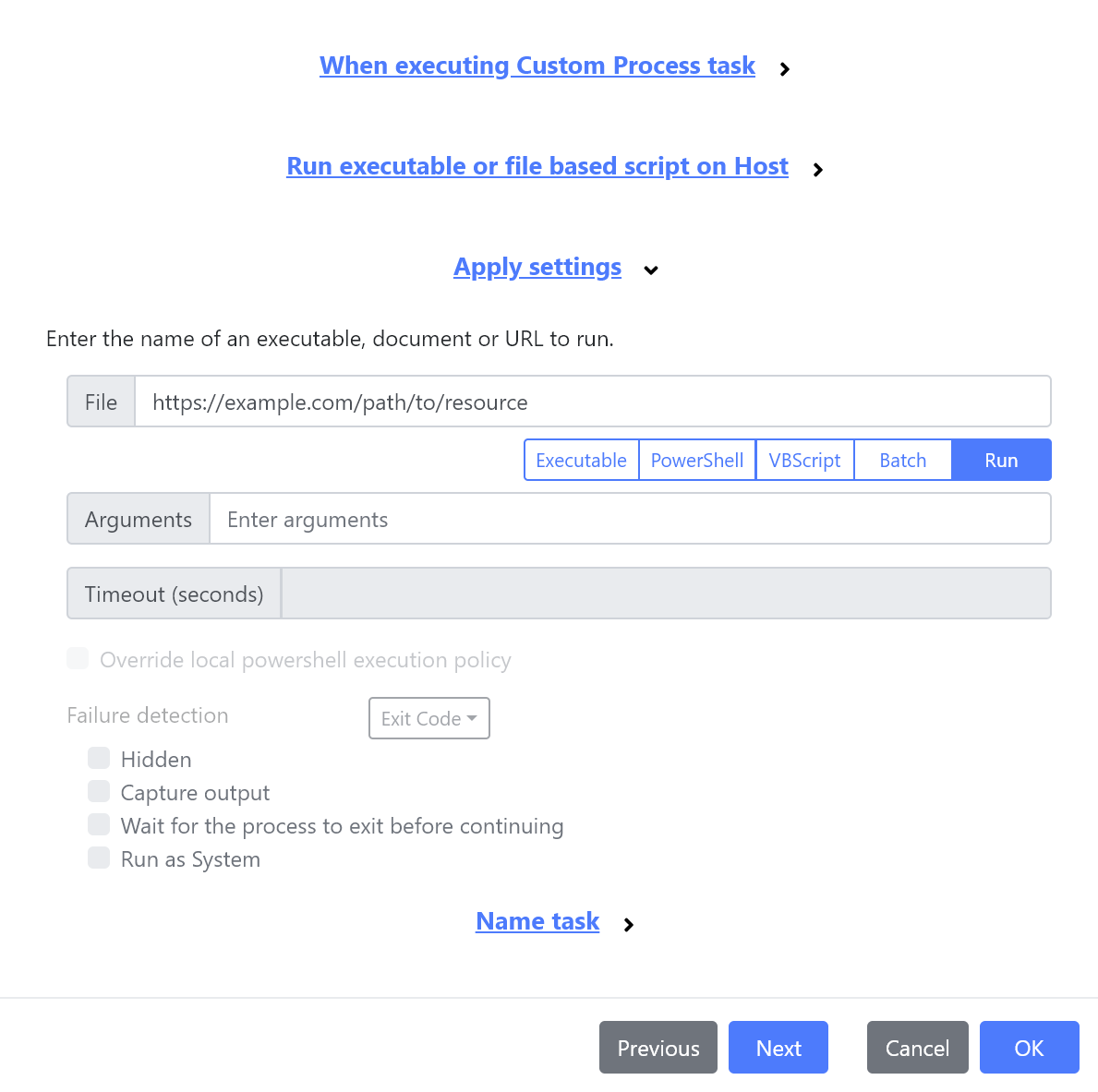
We’ve also added a new Run type which produces the same results as the Operating System’s Run command, enabling it to launch processes, documents or even URL’s.
Named Triggers and Custom Buttons
Whenever access is denied to the shell, it is essential that the user understands the reason and also is able to take steps to resolve the issue. To facilitate this, we’ve introduced the concept of Named Triggers and Custom Buttons. Named Triggers allow a named sequence of tasks to be defined, whilst Custom Buttons can be added to the conditional access screen which when pressed by the user result in the execution of a Named Trigger. By using these features with the Enhancements to Custom Process task, it is easy to launch web pages or control panel applications on the client in response to a button click within the virtual session.
Home Office template
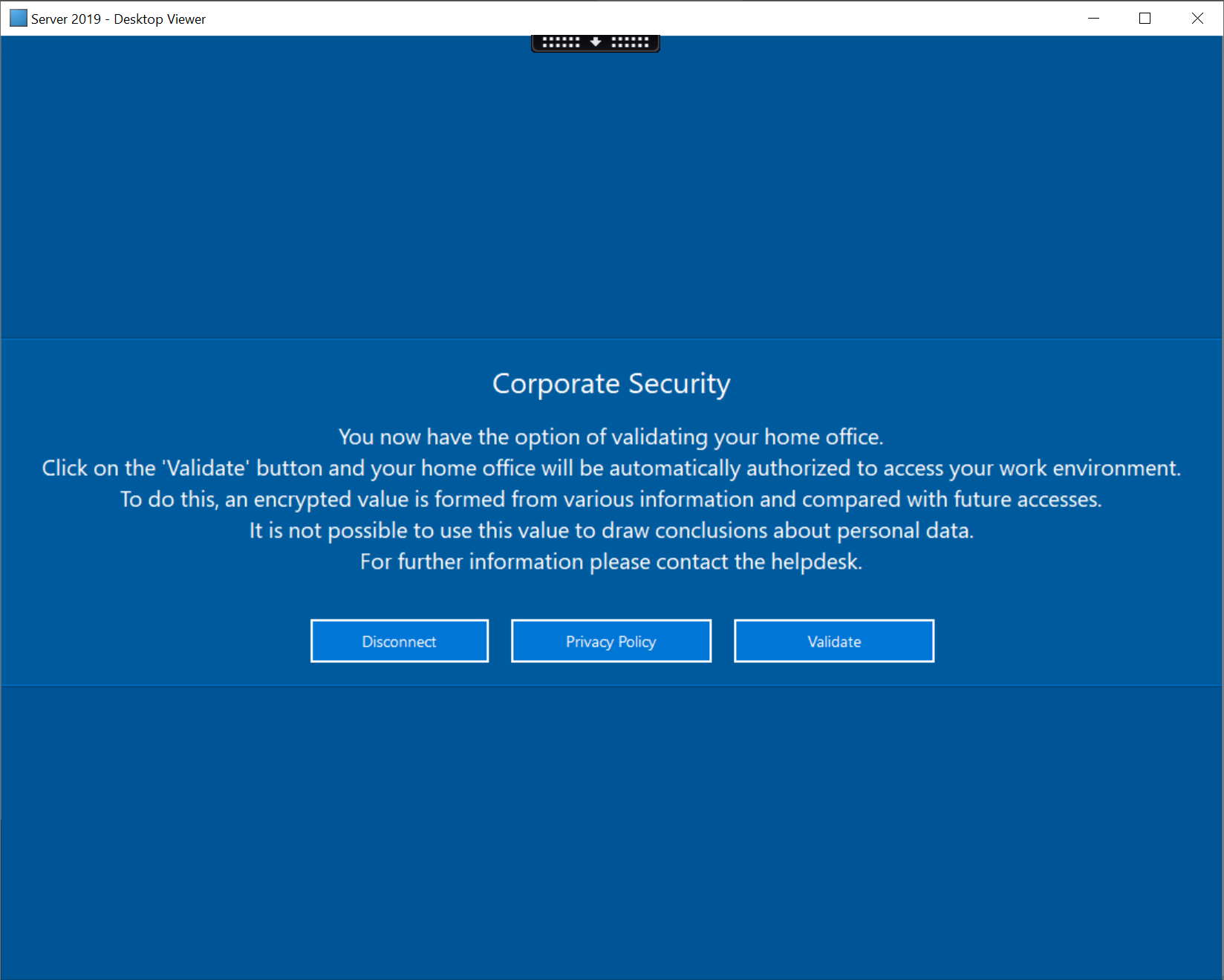
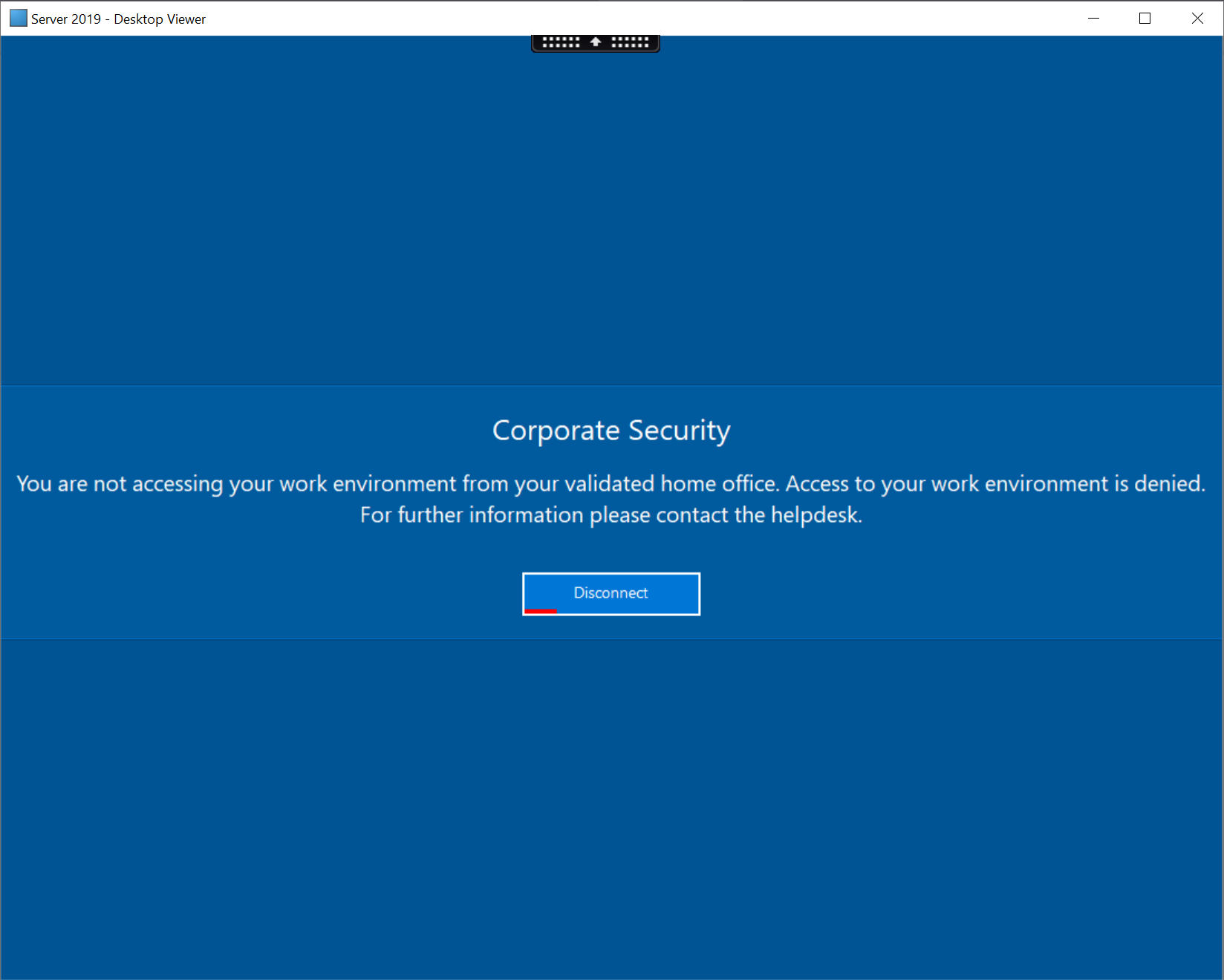
Users are increasingly accessing their workplace from their home office, which poses the challenge to the IT administrator of being able to define the home office of the user. We’ve added a new Home Office template which performs compliance checks to ensure that the remote device meets all compliance requirements. Once compliance requirements are met, external users are given the chance to self-authorize their home office for external access. Once complete, all external access from the user must be performed from the same home office.
Enhancements to Printer task
We’ve had great feedback regarding the Printer task introduced in deviceTRUST 19.3, so we’ve extended the task with the option to specify failover printers when mapping or setting the default printer. The failover printers are used whenever there is an error mapping or setting the default primary printer.
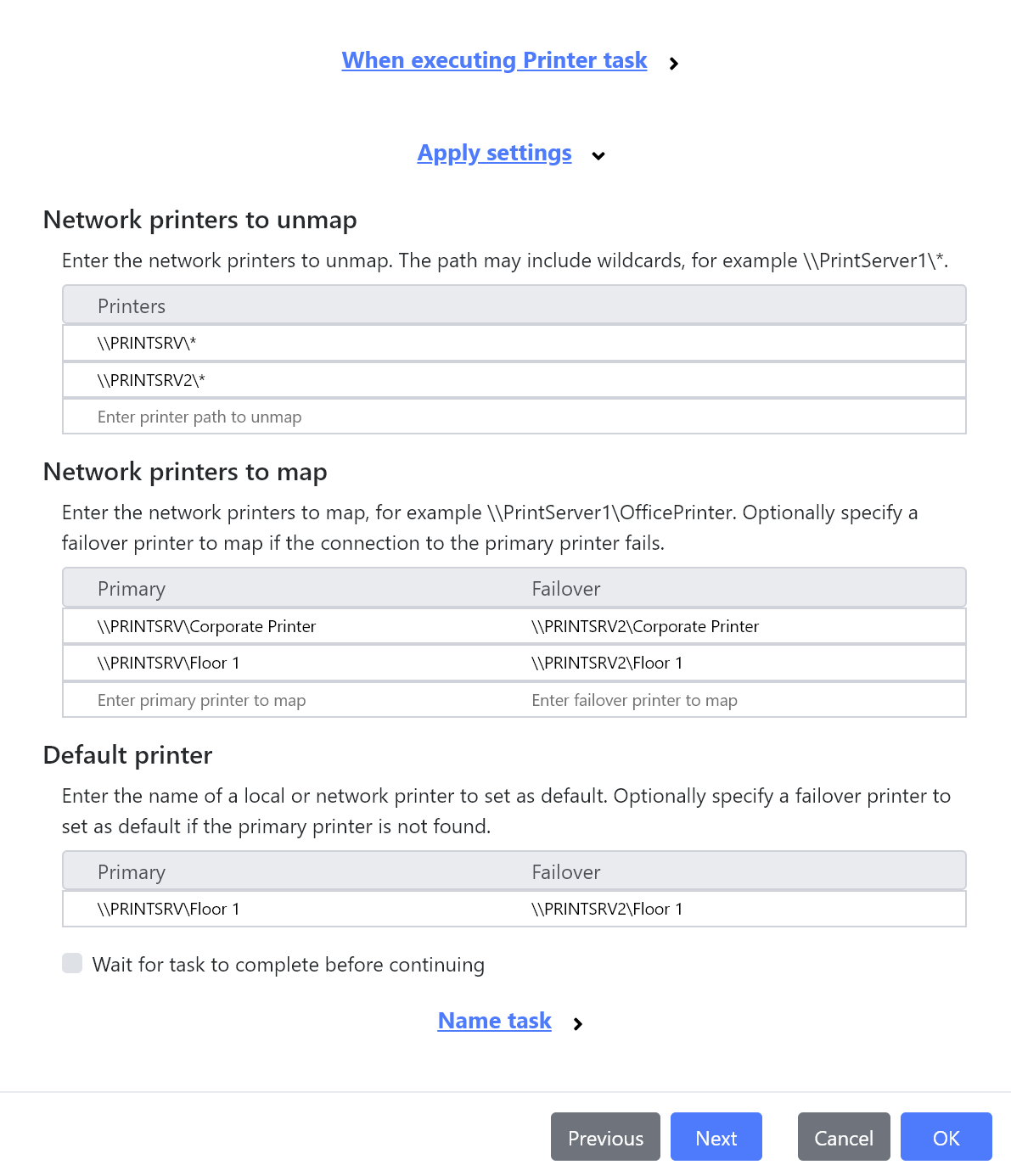
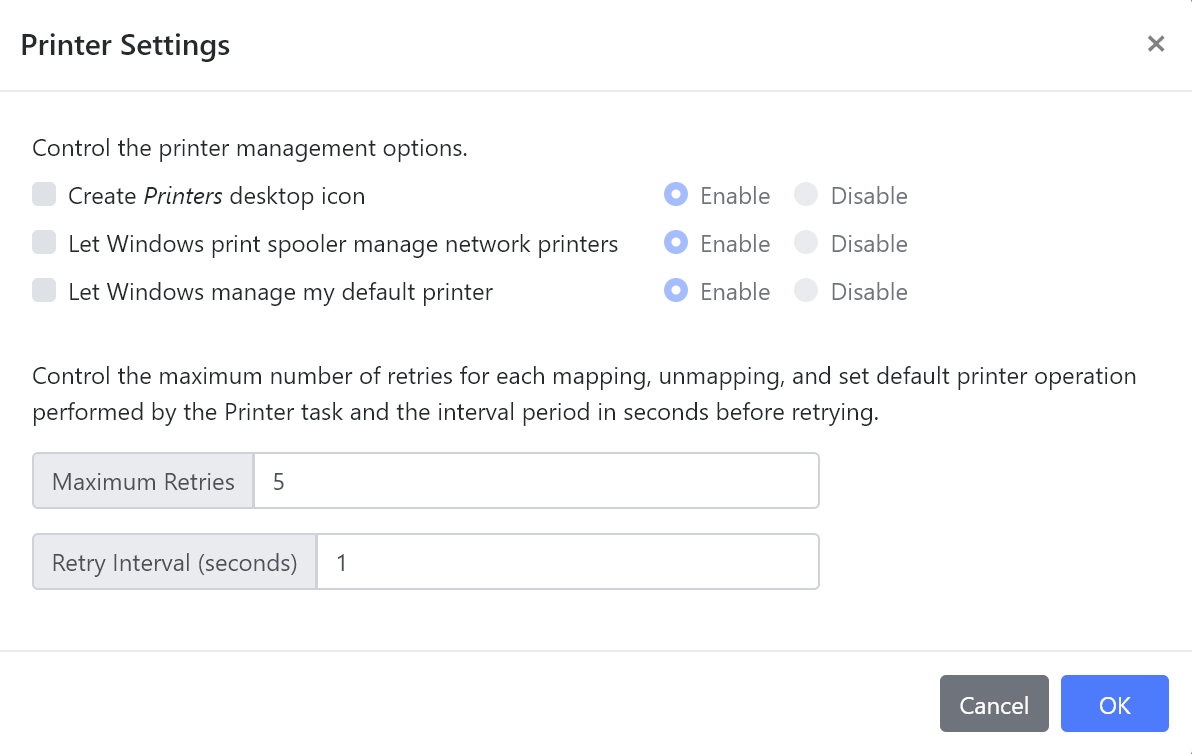
We’ve also included new Printer Settings which includes the following policy items:
-
Create Printers desktop icon - When enabled, extends the Desktop with the Printers icon for all users by creating the registry key
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Desktop\NameSpace\{2227a280-3aea-1069-a2de-08002b30309d}. -
Let Windows print spooler manage network printers - When disabled, sets
RemovePrintersAtLogoffto0withinHKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Print\Providers\Client Side Rendering Print Provider. When enabled this value is removed. Disabling prevents the Operating System from conflicting with changes made via policy. -
Let Windows manage my default printer - When disabled, sets
LegacyDefaultPrinterModeto1withinHKCU\Software\Microsoft\Windows NT\CurrentVersion\Windowsfor all users. When enabled this value is set to0. Disabling prevents the Operating System from conflicting with changes made via policy.
Additionally, we’ve added control for the retry count and timeout periods when mapping or setting the default printer.
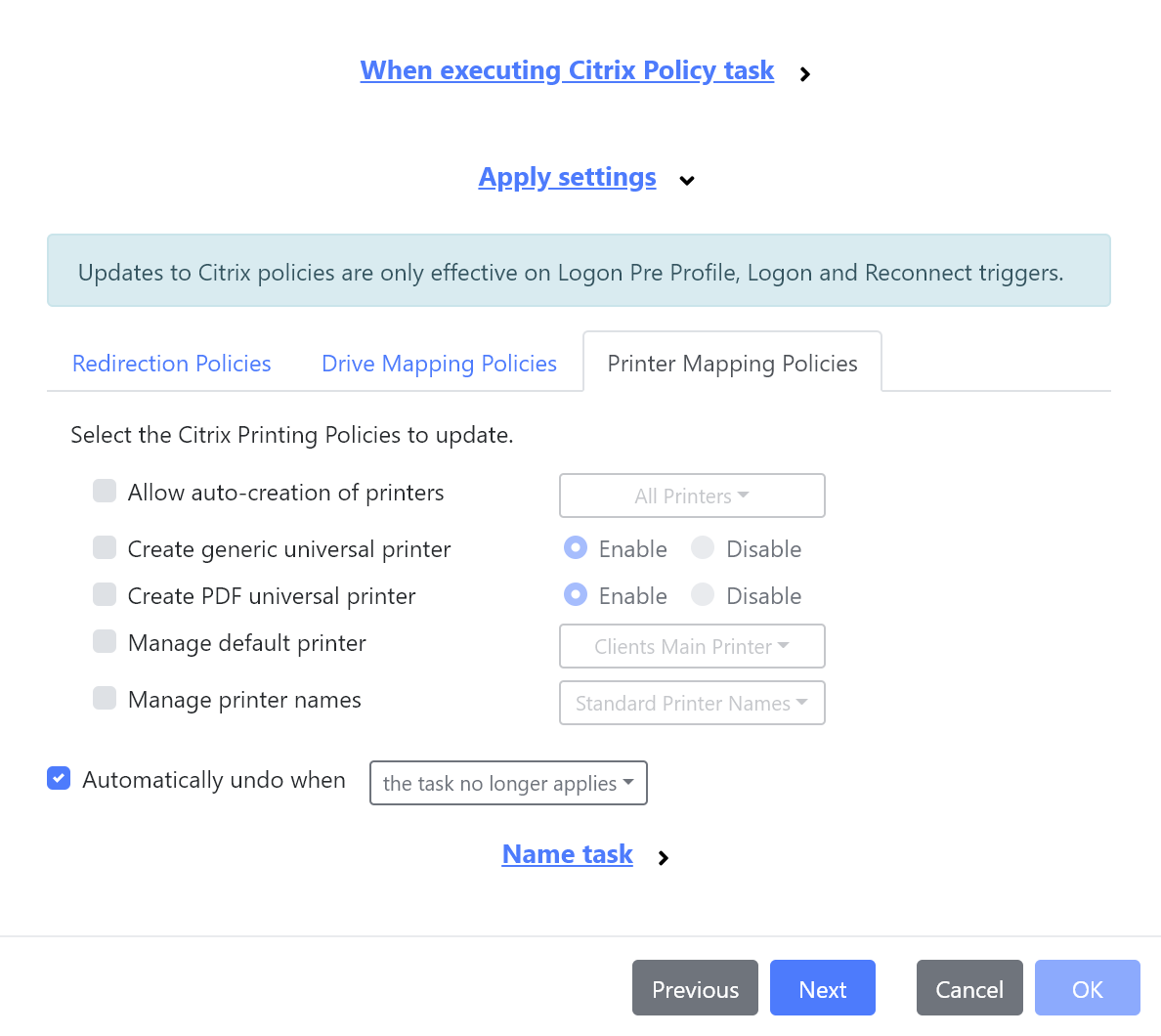
Enhancements to Citrix Policy task
We’ve added support for managing Printer Mapping Policies to the Citrix Policy task.
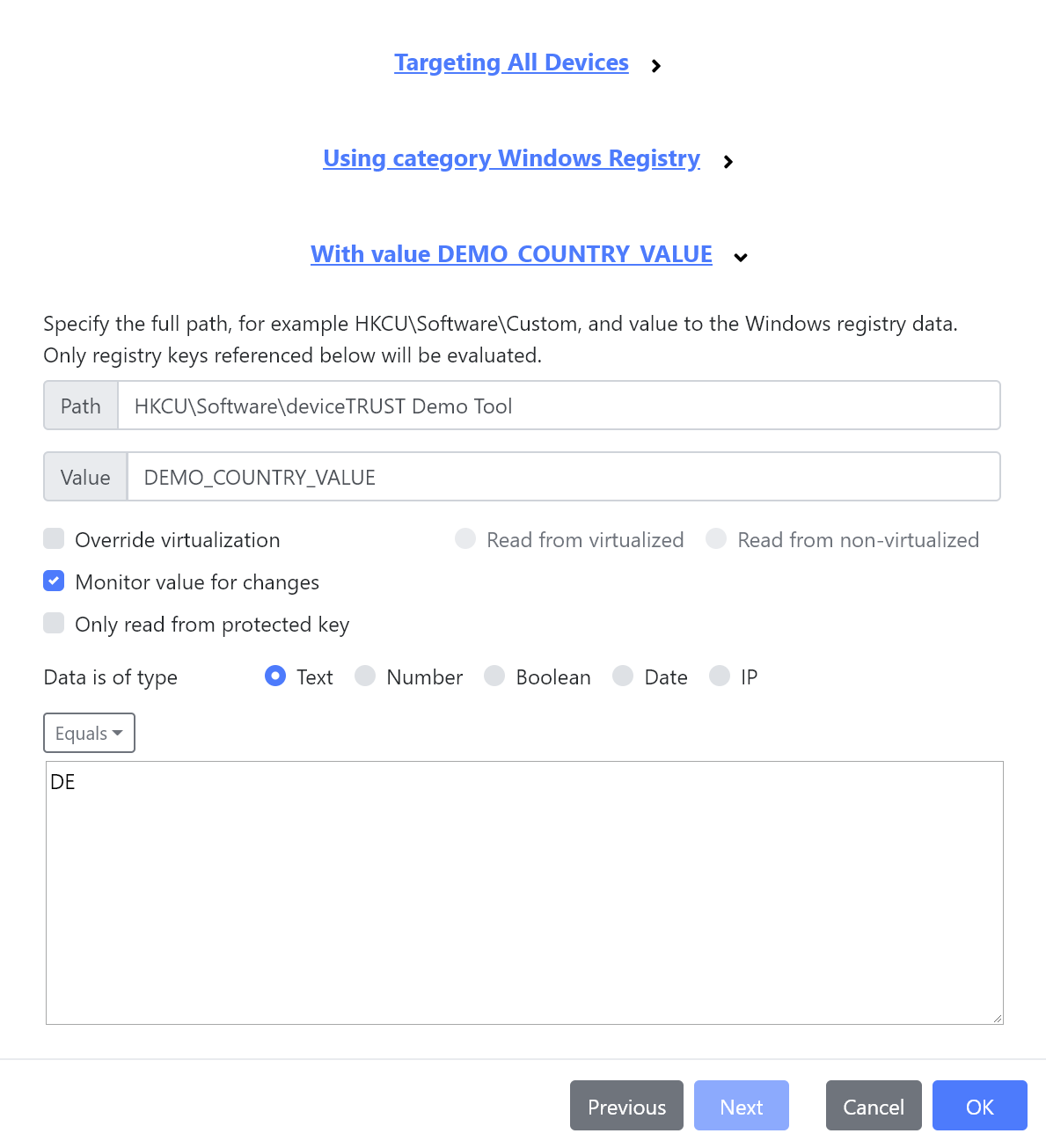
Simplifications to Windows Registry and Security Group conditions
Windows Registry conditions for the host or remote device can now be made directly within the condition editor without the need for the upfront definition within the ADMX. We’ve also added support for monitoring these values, ensuring changes result in an immediate detection of the new value.
The same behavior has been added to the host’s user security group condition.
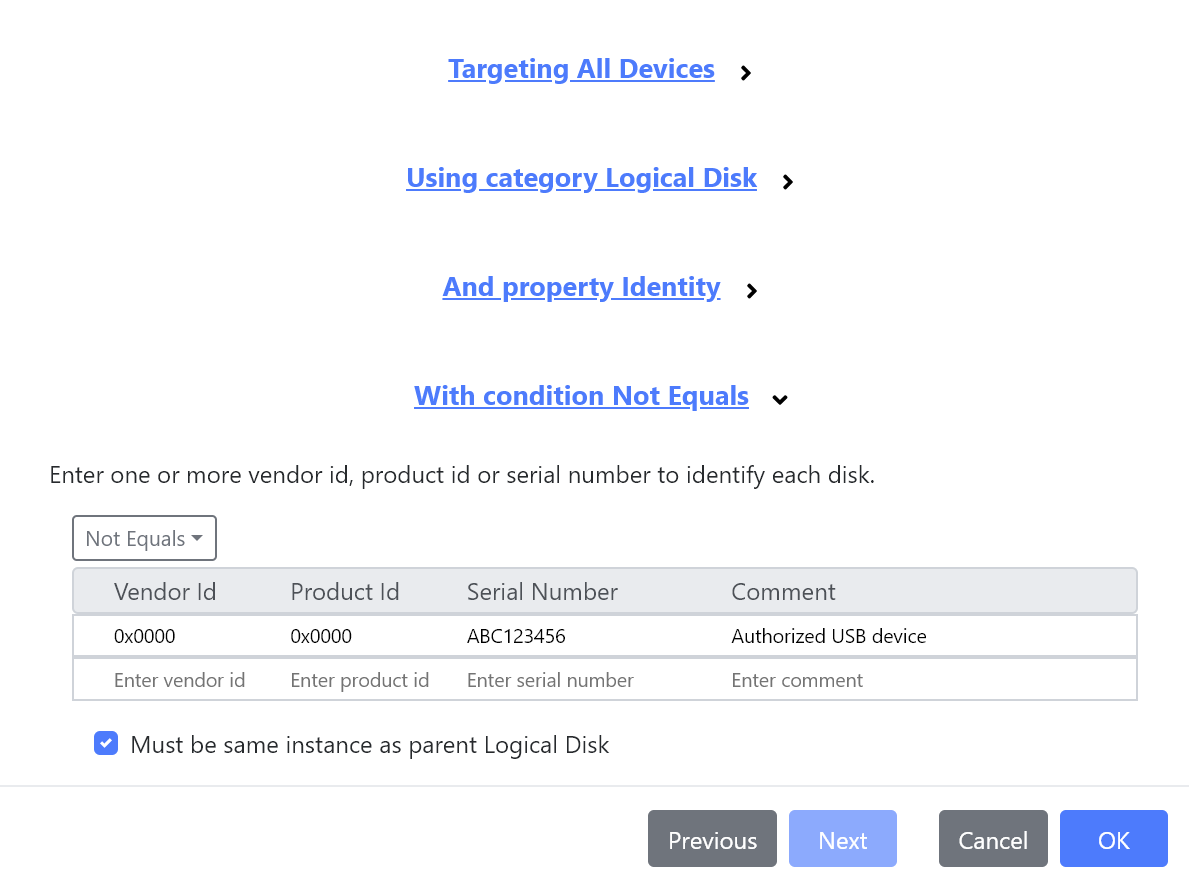
Simplifications to Logical Disk identity
To simplify the identification of logical disks, we’ve introduced a new Identity condition which allows any combination of Vendor Id, Product Id and Serial Number to be defined for a logical disk.
Automatic revert of a task when context no longer applies
A new option to revert tasks ‘when the task no longer applies’ has been added to all tasks that support the behavior, include the Citrix Policy, Deny Access, FSLogix App Masking, Microsoft AppLocker, Screen Saver and Windows Registry tasks. When the context filter for an action is no longer valid, the task will be automatically reverted, simplifying actions by removing the need for corresponding revert tasks.
Visibility of applied policies
Any deviceTRUST policies deployed via GPO or local policy now create a unique registry key at HKLM\Software\Policies\deviceTRUST\Policies which defines:
- ConsoleVersion - The version of the console that saved the policy.
- PolicyName - The name of the policy applied.
- PolicyPath - The LDAP path to the policy within Active Directory.
- PolicyType - Set to either Group Policy or Local Policy.
- TimeStamp - The UTC date that the policy was saved.
- UserName - The name of the user that last saved the changes.
Bug Fixes
- Fixed an issue where applications that were denied using the AppLocker task, could still be run shortly after Logon or Reconnect.
- Fixed an issue where AppLocker rules could be applied when no other rules exist, such as the default rules. This resulted in the OS unable to launch processes critical to the creation of new user sessions.
- Fixed an issue where the 32-bit deviceTRUST Client did not load into a Citrix ICA session unless the Visual C++ 2017 runtimes were installed locally.
- Fixed various issues when locking the desktop when deviceTRUST was denying the user access to the desktop of an endpoint.
Known Issues
- When using an ICA client, because Custom Process Run operations are executed from within a 32-bit process, running documents may have a different behavior to when launched from the Operating System’s Run dialog box. This can be seen when supplying for example ‘firewall.cpl’ as the file name to run, which fails in the same way as as calling ‘START firewall.cpl’ from a 32-bit command prompt. To workaround the issue, aim to execute a process instead, such as a filename ‘control.exe’ with arguments ‘firewall.cpl’.
- The Home Office template fails out of the box on Amazon WorkSpaces. To workaround the issue, remove all Access Mode context filters from both home office actions.
- The deviceTRUST Client installation does not detect the public beta of Amazon WorkSpaces v3. To workaround the issue, manually copy the file C:\Program Files (x86)\deviceTRUST\Client\Bin\dtclient.dll into the folder C:\Program Files (x86)\Amazon Web Services, Inc\Amazon WorkSpaces\vchan_plugins.
Policy Compatibility
The deviceTRUST Host 19.3 and earlier releases are not compatible with policies created by the deviceTRUST Console 19.4. It is recommended that the deviceTRUST Host is upgraded before applying any policy changes.
ADMX Reduction
We’ve removed a number of policy items from ADMX as we move to simplify the user experience and transition to the deviceTRUST Console introduced in 19.1. These changes include:
- PowerShell execution policy has moved from a global ADMX definition into the Custom Process task.
- The ‘Delay Citrix Policies on LOGON and RECONNECT’ is now performed automatically.
- All triggers have been removed.
- All ‘dtcmd.exe’ based security policies have been moved under a single Security node.
Property Changes
The deviceTRUST Console now validates all context conditions and will display a validation warning if properties from previous releases are referenced.
The following properties have been changed:
- MULTIHOP_COUNT is no longer available unless HOST_DEVICETRUST_CONNECTED is TRUE.
- HOST and DEVICE_CUSTOM properties are no longer available for Windows clients. Instead, use the ‘Windows Registry’ conditions.
Where these properties are referenced within a context condition, the existing condition should be removed and replaced accordingly.
