deviceTRUST 20.1.110
This release includes new features and bug fixes to the deviceTRUST Console, Host and Client for Microsoft Windows. For upgrading users, please refer to Compatibility for important changes in this release.
The deviceTRUST 20.1.110 update includes an additional backwards compatibility change for the host and client when using the DEVICE_WINDOWS_UAC property, and a fix to ensure that the console displays clearer error messages when working with properties from 19.4 that have been removed. No changes were made to the Group Policy Administrative Templates within this update.
- New Map Drive task
- New Shortcut task
- New Windows Firewall task
- New Windows Policy task
- New Custom Properties setting
- Licensing, Managed Users, Persistence and System Messages moved from ADMX into the deviceTRUST Console
- Only read properties used within contexts and actions
- Enhancements to Security Product properties
- Enhancements to Network properties
- Enhancements to Location properties
- Enhancements to Windows properties
- Other new Properties
- Citrix Workspace Per-User Installer
- Other minor changes
- Bug Fixes
- Compatibility
New Map Drive task
We’ve added a new Map Drive task which allows control for the contextual mapping and unmapping of network paths. Much like our Map Printer task, this has built in control for failover network paths in the event that a network path is unavailable.
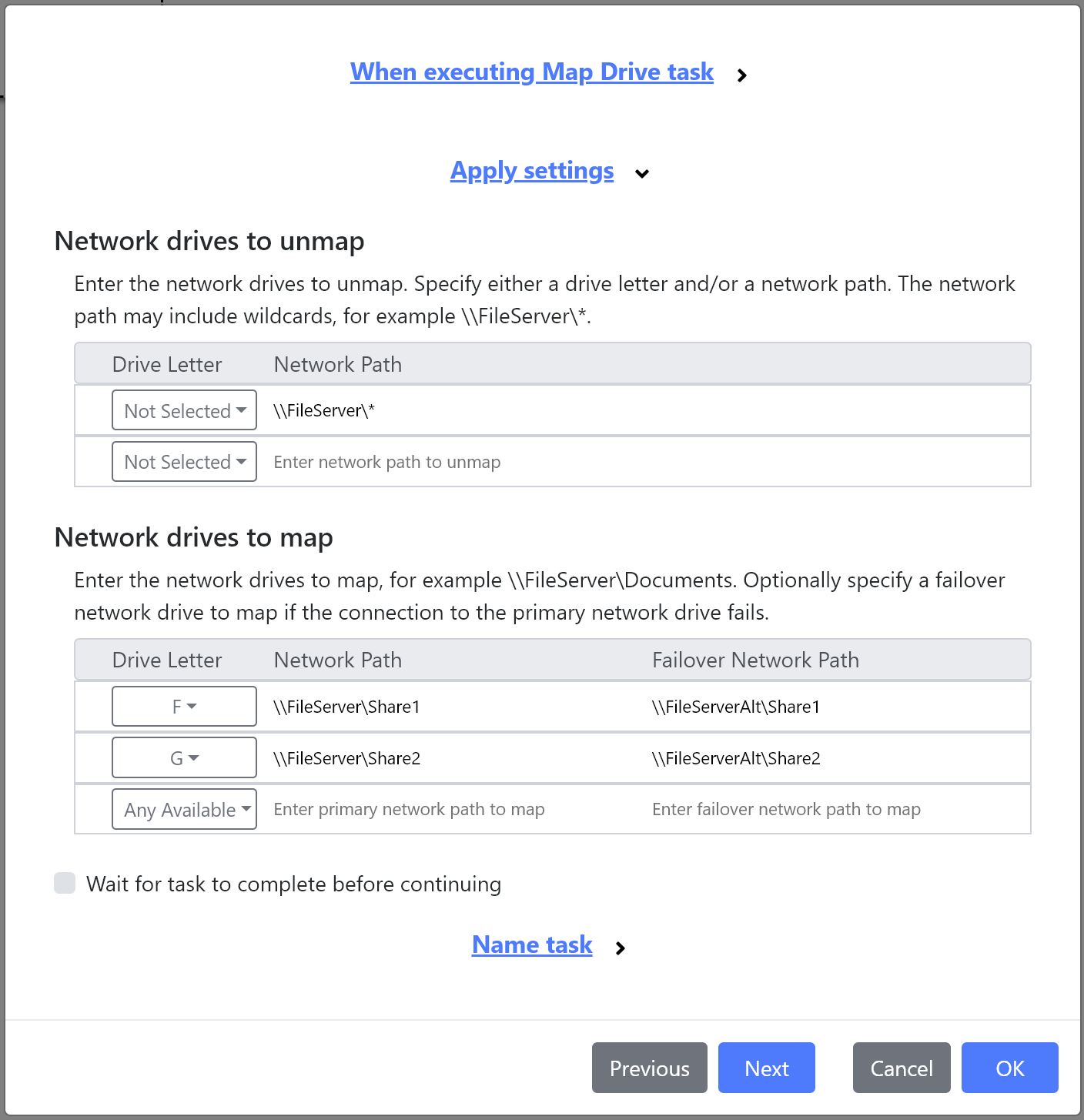
New Shortcut task
The new Shortcut task can be used to create and delete shortcuts to both executables and URL’s. This new task works great with our Microsoft AppLocker or the new Windows Firewall task, by automatically creating shortcuts whenever the target file or URL is available to the user.
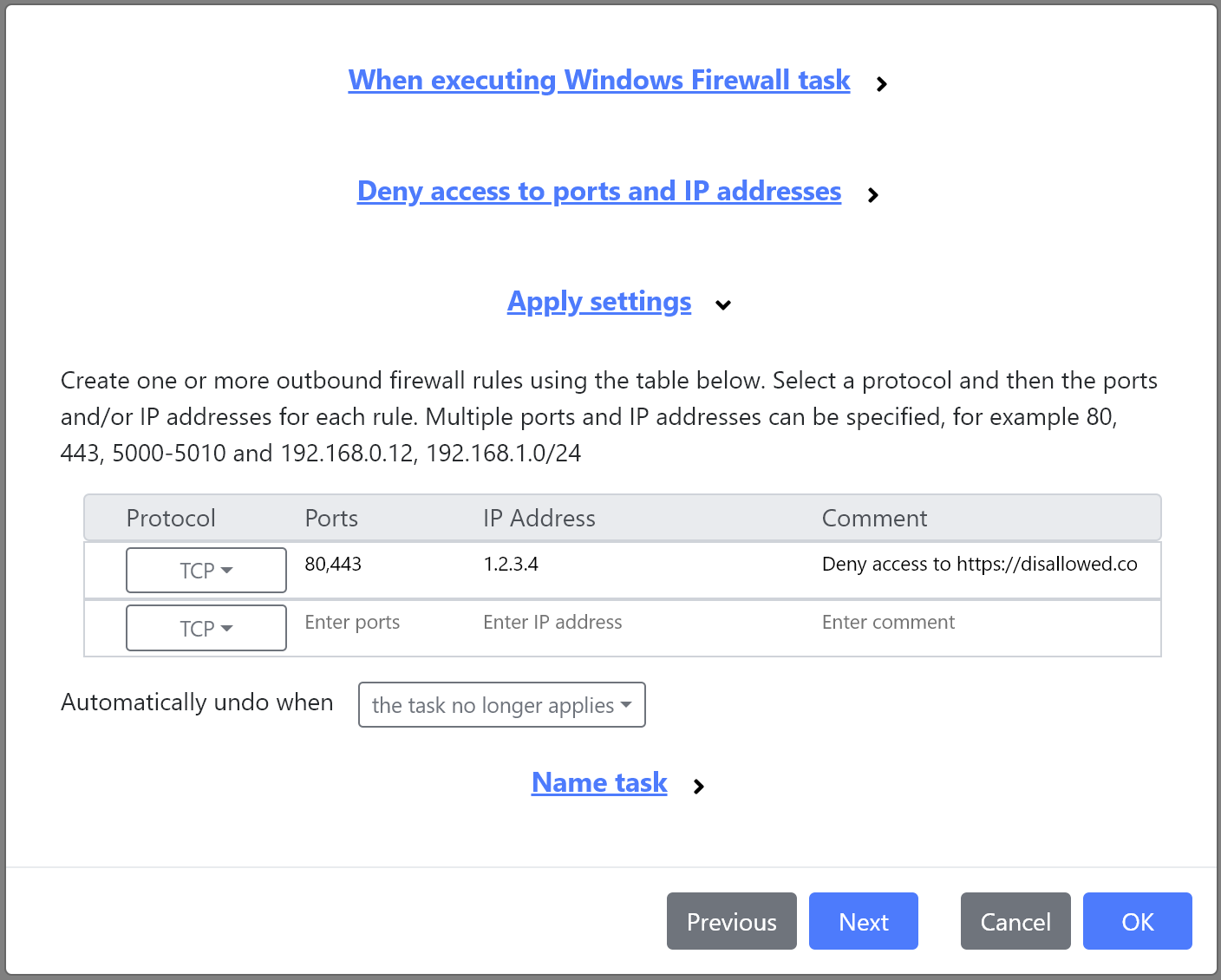
New Windows Firewall task
The new Windows Firewall task can be used to contextually add Windows Firewall rules for the logged in user, controlling access to network ports and addresses.
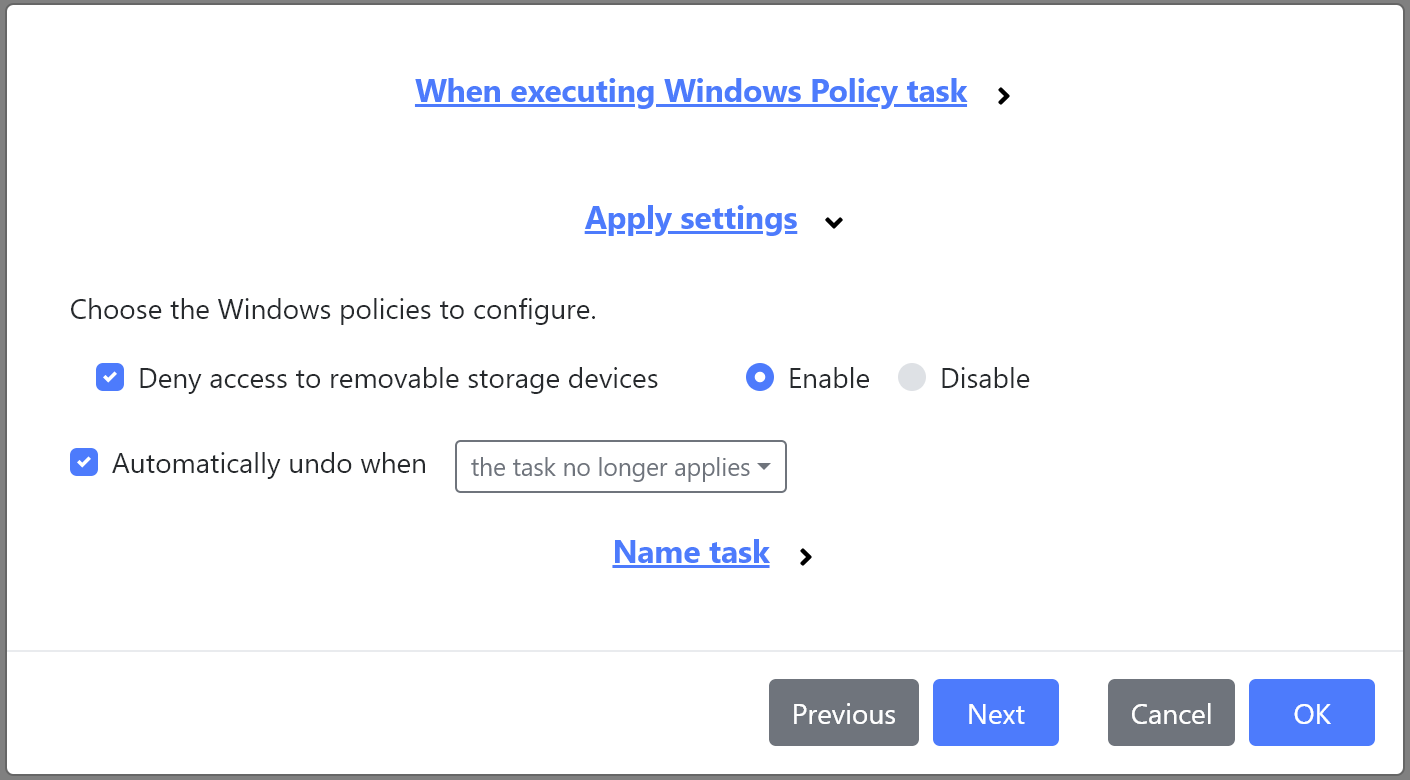
New Windows Policy task
We’ve added a new Windows Policy task that can deny access to removable storage devices.
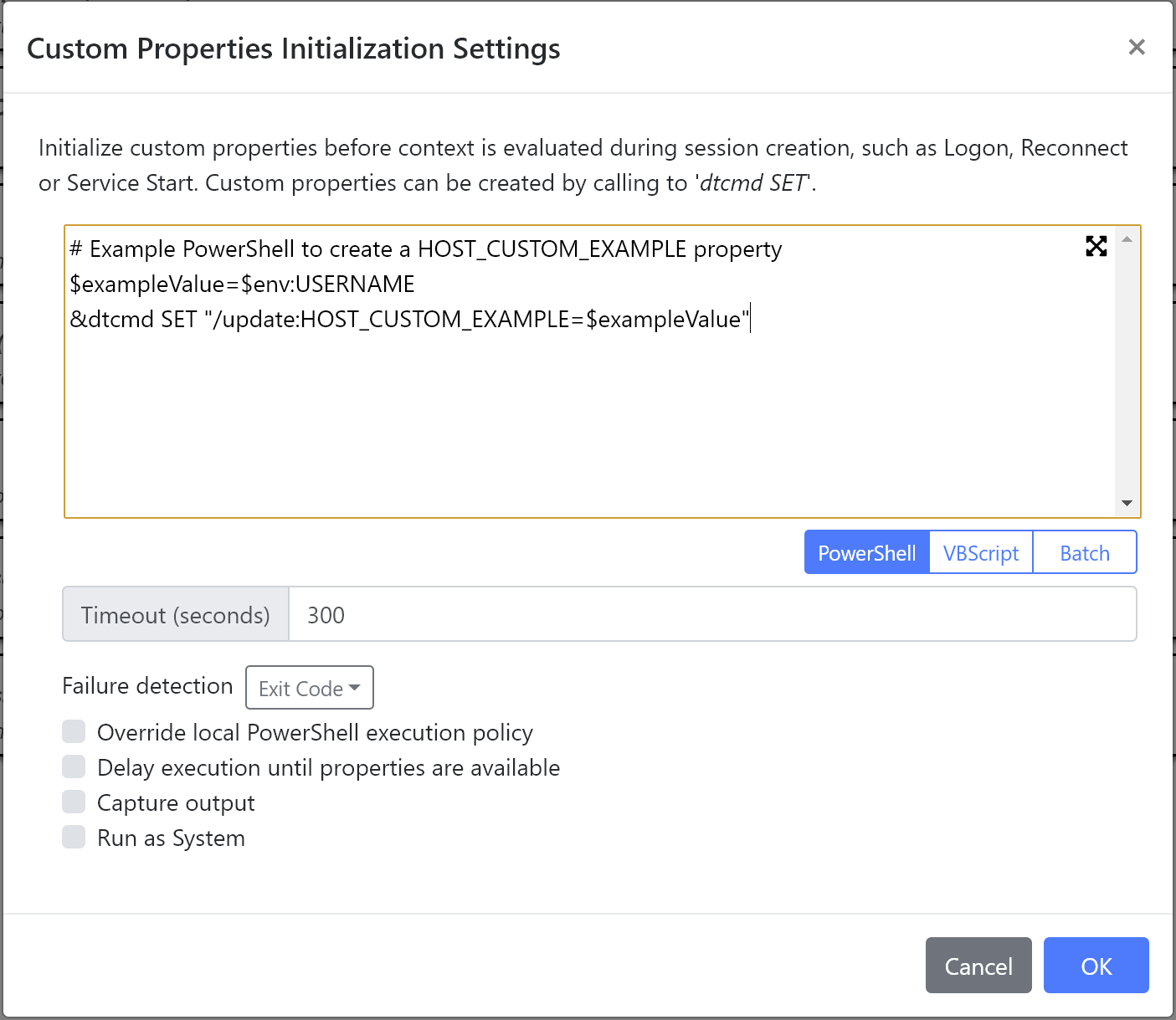
New Custom Properties setting
The new Custom Properties setting allows properties to be defined within a PowerShell, VBScript or Batch file. This script is executed during Logon and Reconnect before the context is defined. This allows information previously inaccessible to deviceTRUST, such as information returned by a web request or a SQL query to be used to define context values.
Licensing, Managed Users, Persistence and System Messages moved from ADMX into the deviceTRUST Console
We’re incrementally moving features from the ADMX Administrative Templates into the deviceTRUST Console. As part of the 20.1 release, we’ve moved Licensing, Managed Users, Persistence and System Messages into the Settings tab of the deviceTRUST Console.
Only read properties used within contexts and actions
deviceTRUST now only reads properties from the host or client that are used within the deviceTRUST Console, removing the need to enable or disable each individual property. This is an important enhancement for simplicity, but also makes it much easier to respect the users privacy by not requesting more information than is required to enforce the necessary business rules. If additional properties are required, perhaps for auditing purposes, then these properties can still be enabled within the ADMX Administrative Templates.
Enhancements to Security Product properties
The Security Product properties have changed format, and we’ve added a couple of layers of caching to ensure an improved end user experience.
The changes to the security product properties are as follows:
- HOST or DEVICE_SECURITYPRODUCT_ANTIVIRUS has been removed.
- HOST or DEVICE_SECURITYPRODUCT_ANTIVIRUS_NAME has been removed.
- HOST or DEVICE_SECURITYPRODUCT_ANTIVIRUS_TIMESTAMP has been removed.
- HOST or DEVICE_SECURITYPRODUCT_ANTISPYWARE has been removed.
- HOST or DEVICE_SECURITYPRODUCT_ANTISPYWARE_NAME has been removed.
- HOST or DEVICE_SECURITYPRODUCT_ANTISPYWARE_TIMESTAMP has been removed.
- HOST or DEVICE_SECURITYPRODUCT_FIREWALL has been removed.
- HOST or DEVICE_SECURITYPRODUCT_FIREWALL_NAME has been removed.
- HOST or DEVICE_SECURITYPRODUCT_COUNT has been added, and is set to the number of security products.
- HOST or DEVICE_SECURITYPRODUCT_X_CATEGORY has been added, and is set to the category of security product, such as Firewall or AntiVirus.
- HOST or DEVICE_SECURITYPRODUCT_X_NAME has been added, and is set to the name of the security product.
- HOST or DEVICE_SECURITYPRODUCT_X_STATUS has been added, and is set to Active, Out-Of-Date or Inactive depending upon the state of the security product.
- HOST or DEVICE_SECURITYPRODUCT_X_TIMESTAMP has been added, and is set to the timestamp of the security product.
This change to an indexed property enables context to perform conditions such as ensuring that the status of a specific product is Active, something that was not possible with the previously delimited properties.
The security products depend upon the Windows Security Center components, which are often not fully initialised until a few minutes after the OS starts up. deviceTRUST 20.1 now caches the security products during logoff and shutdown, and uses the cache whenever the Windows Security Center has not yet initialised during the first few minutes after computer startup.
In addition, we’ve seen some AntiVirus products temporarily become inactive for a few seconds during an update. To ensure a users access to their session isn’t unnecessarily disrupted, we’ve added an in-memory cache which is used to suppress security products that become temporarily inactive.
Enhancements to Network properties
The Network properties representing the IP address have changed format. The previous HOST or DEVICE_NETWORK_X_IP property contained a combination both the IPv4 and IPv6 addresses, and also the subnet mask as part of the CIDR notation postfix. Too much information within this single property made it difficult to consume. We’ve also included a new virtual property which identifies whether the network adapter is not attached to a physical device.
The changes to the network properties are as follows:
- HOST or DEVICE_NETWORK_X_IP has been removed.
- HOST or DEVICE_NETWORK_X_IPV4_ENABLED has been removed.
- HOST or DEVICE_NETWORK_X_IPV6_ENABLED has been removed.
- HOST or DEVICE_NETWORK_X_IPV4 has been added, and represents a semi-colon separated list of IPv4 addresses bound to the network adapter.
- HOST or DEVICE_NETWORK_X_IPV6 has been added, and represents a semi-colon separated list of IPv6 addresses bound to the network adapter.
- HOST or DEVICE_NETWORK_X_IPV4_SUBNET has been added, and is set to the IPv4 address masked with the subnet and with the subnet prefix length appended in CIDR notation. For example, an IP address of 192.168.10.12 with subnet 255.255.255.0 will be set to a value of 192.168.10.0/24. This new value becomes an accurate check of whether a device is part of a specific network.
- HOST or DEVICE_NETWORK_X_IPV6_SUBNET has been added, and is set to the IPv6 address masked with the subnet and with the subnet prefix length appended in CIDR notation.
- HOST or DEVICE_NETWORK_X_VIRTUAL has been added, and represents whether the network adapter is not attached to a physical device.
Enhancements to Location properties
We’ve replaced the previous latitude and longitude with a new position property, and introduced new In Range and Not In Range operators within context conditions. This allows a context to easily determine whether a device is within range to a specific place of work.
The changes to the location properties are as follows:
- HOST or DEVICE_LOCATION_LATITUDE has been removed.
- HOST or DEVICE_LOCATION_LONGITUDE has been removed.
- HOST or DEVICE_LOCATION_POSITION has been added, and is set to the combination of latitude and longitude, such as “49.8629,8.6203”.
Enhancements to Windows properties
Our previous Windows Update, UAC and Zone Settings properties were built on top of Windows Security Center which is unavailable on Server OS’s. We’ve therefore re-worked these properties in 20.1 removing our dependency on Windows Security Center.
The changes to the Windows properties are as follows:
- HOST or DEVICE_WINDOWS_UPDATE has been removed.
- HOST or DEVICE_WINDOWS_UAC has been removed.
- HOST or DEVICE_WINDOWS_ZONESETTINGS has been removed.
- HOST or DEVICE_WINDOWS_UAC_ENABLED has been added, and is set to true if the User Access Control (UAC) consent prompt is enabled.
- HOST or DEVICE_WINDOWS_UAC_POLICY has been added, and defines the User Access Control (UAC) consent prompt policy applied to administrators.
Other new Properties
We’ve added more new properties, including information about the remote device and user attributes queried from Active Directory:
- HOST or DEVICE_CERTIFICATE_X_POLICIES - The certificate policies identifying the intended purpose of the certificate.
- HOST or DEVICE_CERTIFICATE_X_TPM_KEY_ATTESTATION - Detects the key attestation issuance policies which prove to a CA that the certificate is protected by a trusted TPM.
- HOST or DEVICE_OS_STARTUPTIME - The time that the OS started.
- HOST or DEVICE_REMOTECONTROL_REMOTE_VERSION - The version number of the remote client on Citrix and VMware only.
- HOST or DEVICE_REMOTECONTROL_REMOTE_INSTALLPATH - The installation path of the remote client on Citrix only.
- HOST or DEVICE_USER_ATTRIBUTE_COUNT - The number of user attributes read from Active Directory.
- HOST or DEVICE_USER_ATTRIBUTE_X_NAME - The name of a user attribute read from Active Directory.
- HOST or DEVICE_USER_ATTRIBUTE_X_VALUE - The value of a user attribute read from Active Directory.
- HOST_DEVICETRUST_LICENSE_VALID - Determines whether the deviceTRUST license is valid.
- HOST_DEVICETRUST_LICENSE_UNIT - The deviceTRUST licensable unit, e.g. a User or Device.
- HOST_DEVICETRUST_LICENSE_TYPE - The deviceTRUST license type.
- HOST_DEVICETRUST_LICENSE_COUNT - The number of deviceTRUST licensed units.
- HOST_DEVICETRUST_LICENSE_ISSUEDATE - The date that the deviceTRUST license was issued.
- HOST_DEVICETRUST_LICENSE_EXPIRYDATE - The date that the deviceTRUST license expires.
Citrix Workspace Per-User Installer
The deviceTRUST Client remains an all users installer, however if Citrix Workspace has been installed as a per user installer, we now correctly register the deviceTRUST virtual channel.
Other minor changes
- The Deny Access task is now prioritised based on the action priority, action name and then finally the sequence position, matching the location that it appears within the deviceTRUST Console. This ensures that the message that appears to the user can be easily anticipated in situations where multiple deny access tasks are executed.
- The Deny Access task can now deny access to administrative users logged into the console session.
- Added support for
No TLSencryption within the Send Mail task. - The deviceTRUST Host service restart policy has been reduced from 30 seconds to 5 seconds.
- The deviceTRUST Host will now relaunch tasks filtered by a context change on service restart.
- The Microsoft AppLocker timeout has been removed from ADMX and added to the Microsoft AppLocker task.
- Added a policy
Remoting protocols that deviceTRUST will use when attempting to establish properties from the remote devicewhich allows individual protocols to be enabled or disabled. - Multiple printers can now be mapped or set as default by supplying comma separated lists of printers within the Printer Mapping task.
- Environment variables are now automatically expanded when used within any of the tasks.
- Added a new policy to toggle Location and Whois for users that are internal, i.e. not accessing through a gateway on Citrix or VMware Horizon environments.
- Added a policy
Remove write access to deviceTRUST Policy for Local Administratorsto remove permissions to theHKLM\Software\Policies\deviceTRUSTregistry key for local administrators. - Popup messages can now display buttons to launch named trigger sequences.
- Added new auditing event
ID 17 - UNMANAGED USERwhen an unmanaged user logs on, andID 3 - POLICY LOADwhen the deviceTRUST Host detects a policy change.
Bug Fixes
Bug Fixes to the deviceTRUST Console in 20.1.100
- Fixed an issue where pasting into the logical disk identity condition always pasted into the Vendor Id field of a new row. Additionally after pasting empty fields would cause the condition to always fail.
- Fixed an issue where where typing within the AppLocker Task’s exceptions field would always create an exception, even if no content was supplied.
Bug Fixes to the deviceTRUST Console in 20.1.110
- Fixed an issue after upgrading a 19.4 configuration containing deprecated properties, where it was unclear which specific properties had been deprecated.
Bug Fixes to the deviceTRUST Host in 20.1.100
- Fixed an issue where the Template property of Certificates was always blank.
- Fixed an issue on VMware Horizon where a black screen could appear when reconnecting to a virtual session.
- Fixed an issue on Citrix where a black screen could temporarily occur whilst denying access to a virtual session.
- Fixed an issue where a black screen could be shown to the user if access to a session was denied whilst the session was transitioning to the screensaver.
- Fixed an issue with the Send Mail task where failure to include the DEVICE_DEVICETRUST_VERSION in the client properties resulted in the email not being sent.
- Fixed an issue where Logon system messages longer than 79 characters could cause the host to crash.
- Fixed an issue where environment variables to custom processes did not expand when the policy
Persist properties to the user environment variableswas disabled. - Fixed an issue where enabling or disabling individual users from the location properties did not work.
- Fixed an issue where the OS could update the policy whilst the deviceTRUST Host was still reading it, resulting in policies potentially being ineffective.
- Fixed an issue where entering comments within the security group conditions would result in failure to detect whether the user was a member of the security group.
- Fixed an issue where the Logon Shell Ready would not trigger, and changes to properties would not be detected when using HP Easy Shell.
Bug Fixes to the deviceTRUST Properties (Host & Client) in 20.1.100
- Fixed an issue with the Logical Disk’s Hidden property, where the user and machine priority were not combined in the same way as was performed by the OS.
- Fixed an issue with the Security Products Firewall status not always being real-time.
- Fixed an issue where the Windows properties UAC value was incorrect.
- Fixed an issue with inaccurate OS description reported to Citrix session.
- Fixed an issue where the Network Gateway Mac included an all zero physical address.
Bug Fixes to the deviceTRUST Properties (Host & Client) in 20.1.110
- Added backwards compatibility to the deviceTRUST Host receiving the old format of Windows UAC property from a 19.4 or earlier deviceTRUST Client.
- Added backwards compatibility to the deviceTRUST Client to send the old format of Windows UAC property to a 19.4 or earlier deviceTRUST Host.
Compatibility
The deviceTRUST Host 19.4 and earlier releases are not compatible with policies created by the deviceTRUST Console 20.1. It is recommended that the deviceTRUST Host is upgraded before applying any policy changes.
The following changes should be carefully considered before upgrading the deviceTRUST Host:
- The deviceTRUST license and managed user list has moved from the ADMX Administrative Templates into the
Settingstab within the deviceTRUST Console. If you previously had these policies defined, then you should migrate the settings to the new Licensing Settings:Enable deviceTRUSTWhitelist of users controlled by deviceTRUSTBlacklist of users not controlled by deviceTRUST
- Local administrator users are no longer managed by default. This can be changed by unchecking
Do not manage local administratorswithin the Licensing Settings. - The following policies have been moved from the ADMX Administrative Templates into the new Persistence Settings. If you previously had these policies defined, then you should migrate the settings to the new location:
Persist properties to a session specific locationPersist properties to the users registryPersist properties to the user environment variableDefine properties which will not be written to the Windows Event Log
- The following policies have been moved from the ADMX Administrative Templates into the new System Messages Settings. If you previously had these policies defined, then you should migrate the settings to the new location:
User message displayed whilst establishing host properties and device identityUser message displayed whilst establishing context with a deviceUser message displayed when a connection from a trusted device is disallowedUser messages displayed when automatically updating the clientUser message displayed when an untrusted device is disallowedUser message displayed on logoff buttonUser message displayed on disconnect buttonUser message displayed on lock buttonUser message displayed whilst triggers are executedTranslations of user message displayed whilst establishing host properties and device identityTranslations of user message displayed whilst establishing context with a deviceTranslations of user message displayed when a connection from a trusted device is disallowedTranslations of user messages displayed when automatically updating the clientTranslations of user message displayed when an untrusted device is disallowedTranslations of user message displayed on logoff buttonTranslations of user message displayed on disconnect buttonTranslations of user message displayed on lock buttonTranslations of user message displayed whilst triggers are executed
- When local administrators are managed users, access to the session can now be denied.
- The format of Security Product properties has changed, see Enhancements to Security Product properties. Please ensure that you update your context conditions, or if using one of our templates then we recommend re-importing that template. Additional information can be found in Updating contexts to the new Security Product properties. Any access of the property external to deviceTRUST, such as in a script or third party product will also need to be updated to reference the new values.
- The format of the Network properties has changed, see Enhancements to Network properties. Please ensure that you update your context conditions, or if using one of our templates then we recommend re-importing that template. Any access of the property external to deviceTRUST, such as in a script or third party product will also need to be updated to reference the new values.
- The format of the Location properties has changed, see Enhancements to Location properties. Please ensure that you update your context conditions, or if using one of our templates then we recommend re-importing that template. Any access of the property external to deviceTRUST, such as in a script or third party product will also need to be updated to reference the new values.
- The format of the Windows properties has changed, see Enhancements to Windows properties. Please ensure that you update your context conditions. Unfortunately we no longer support the
Internet Explorer Zone Settingsproperty, however theUACproperty can be updated with its equivalent and theUpdateproperty can be updated with properties from theWindows Updatecategory. - Support for Custom device properties has been removed from the deviceTRUST Console. If you are using Custom properties with IGEL or eLux, then please wait for the forthcoming release of the IGEL and eLux 20.1 clients.
-
String EqualsandString Not Equalsconditions no longer accept wildcards. If you previously used wildcards from within a condition then please ensure that you are using theWildcard EqualsorWildcard Not Equalsconditions. - The property changed trigger has been removed. Please ensure you model your properties with a context and use the context changed trigger instead.
- The
Propagate MULTIHOP propertiespolicy is now disabled by default. - The policy
Timeout whilst waiting for AppLocker to process a changehas been removed. The timeout value can now be specified on the Microsoft AppLocker task. - An additional Active Setup
deviceTRUST Citrix Cleanup 32-bitcomponent has been added. More details can be found here.
Compatibility between deviceTRUST Host 20.1 and deviceTRUST Client 19.4 or earlier
The deviceTRUST Host 20.1.100 will automatically convert Security Product, Network and Location properties received from a 19.4 deviceTRUST Client into the latest format. Additionally, the deviceTRUST Host 20.1.110 will automatically convert the Windows UAC property received from a 19.4 deviceTRUST Client.
Compatibility between deviceTRUST Client 20.1 and deviceTRUST Host 19.4 or earlier
The deviceTRUST Client 20.1.100 will automatically send the previous format of Security Product, Network and Location properties when connecting to a 19.4 or earlier deviceTRUST Host. Additionally, the deviceTRUST Client 20.1.110 will also send the previous format of Windows UAC property to a deviceTRUST 19.4 or earlier Host.
Updating contexts to the new Security Product properties
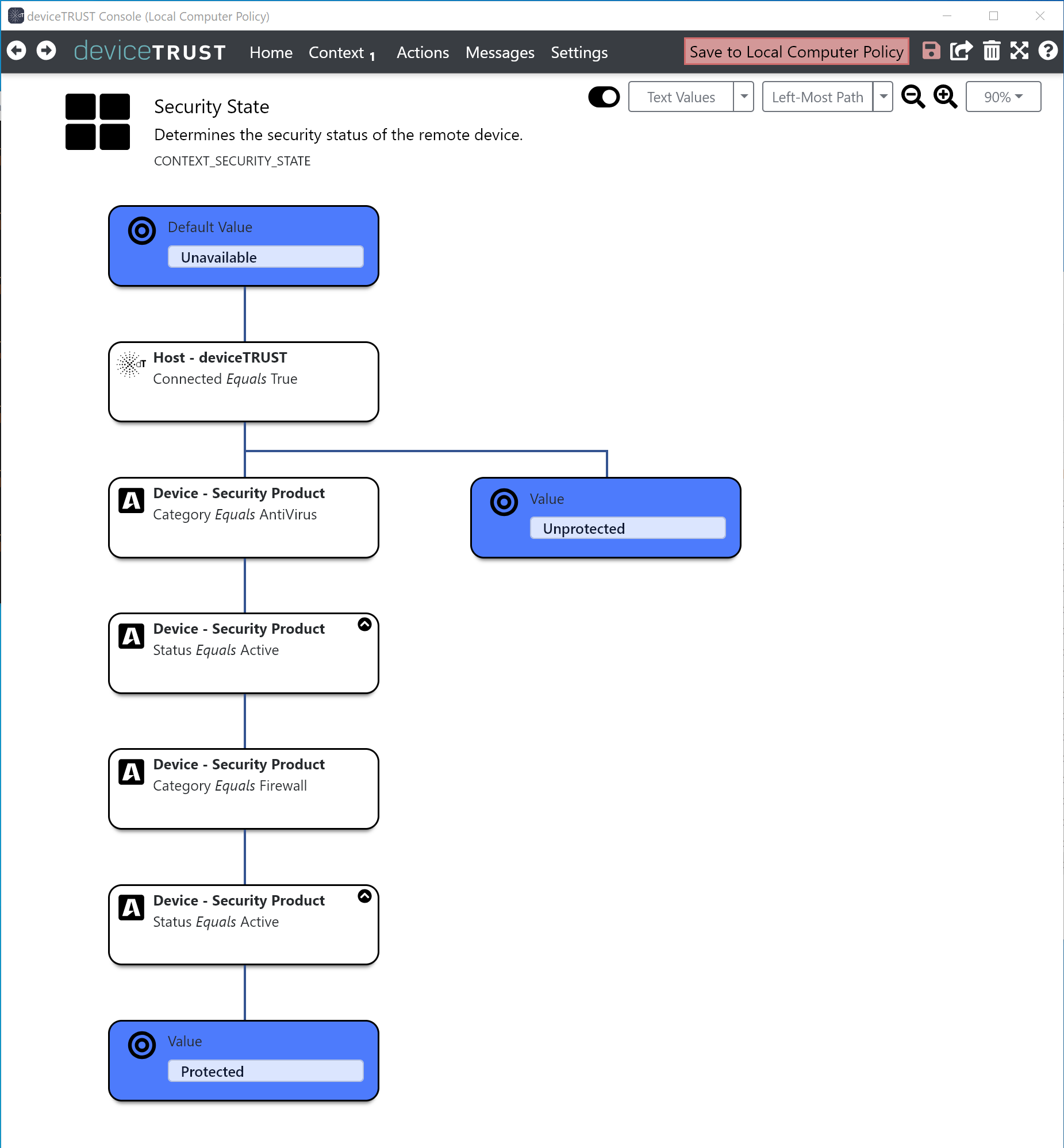
As detailed in Enhancements to Security Product properties, we’ve made significant changes to our Security Product properties which may need special attention. If you were previously using the Security State template from deviceTRUST 19.4, then you can avoid the need to update your contexts by using our Security State for Remote Devices template from deviceTRUST 20.1 which is available within the Compliant Access template category. However if you want to update an existing context then please continue below.
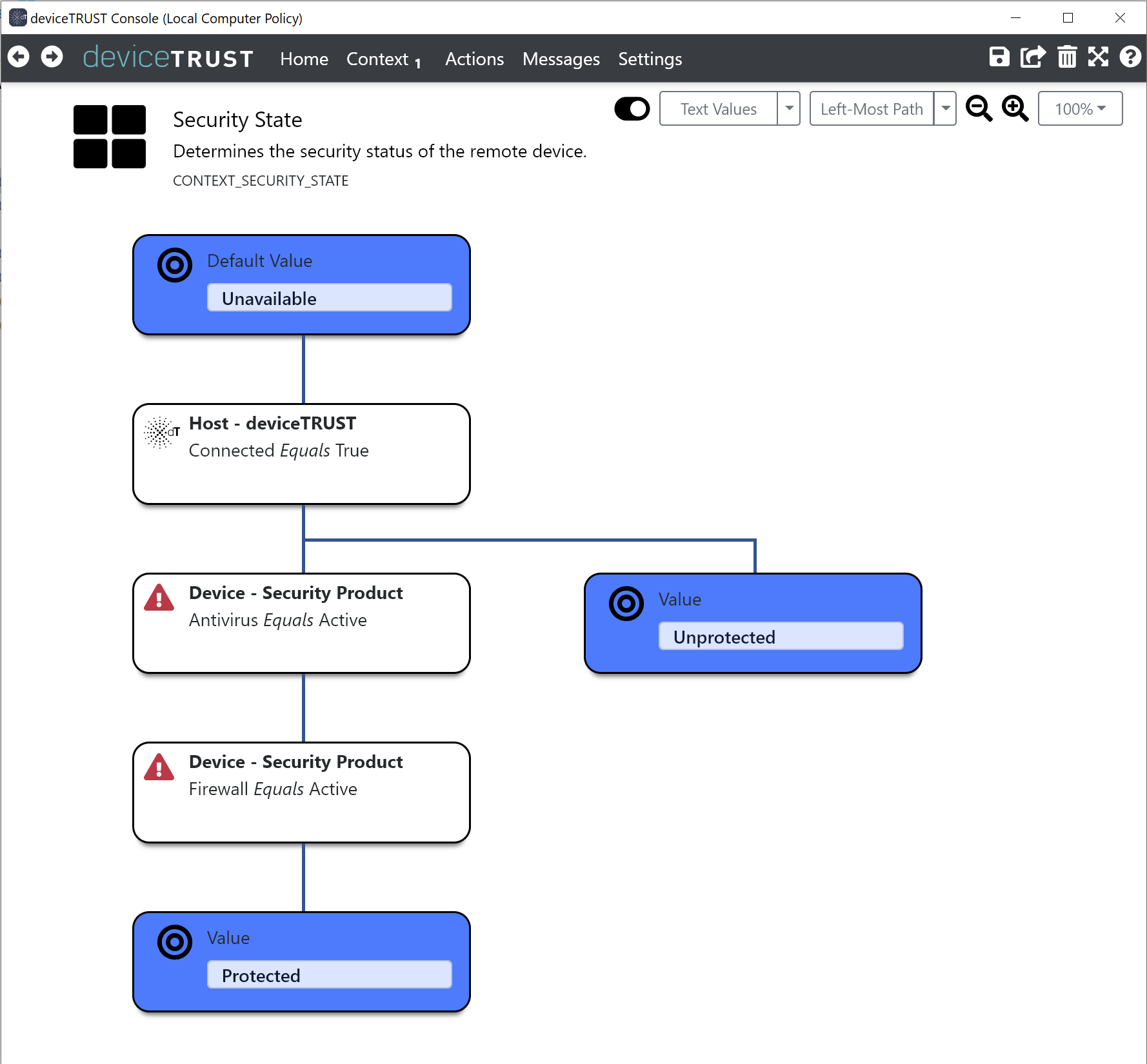
The above screenshot shows an example context built on the old Security Products after upgrading the deviceTRUST Console to 20.1. Note that both the Device - Security Product - Antivirus Equals Active and Device - Security Product - Firewall Equals Active properties have a warning symbol highlighting a problem. If you attempt to edit the property, the error message Referenced property in category 'Security Product' is no longer valid. Please select a different property is displayed.
To update the Device - Security Product - Antivirus Equals Active condition:
- Click on the
+below the condition to insert a new condition.- Select
All Devicesand then click on theSecurity Productcategory. - Select the
Categoryproperty. - Ensure that the operator is
Equalsand only theAntivirusvalue is checked. - Click
OK.
- Select
- Click on the
+below the new condition to insert another new condition.- Select
All Devicesand then click on theSecurity Productcategory. - Select the
Statusproperty. - Ensure that the operator is
Equalsand only theActivevalue is checked. - Check the option
Must be the same instance as parent Security Product. This is essential to ensure that this condition only matches the same security product that hasCategory Equals Antivirus. - Click
OK.
- Select
- Delete the previous condition
Device - Security Product - Antivirus Equals Active
Repeat the above steps, this time replacing the Device - Security Product - Firewall Equals Active condition and choosing the Category property to equal Firewall.
After following the steps, the updated configuration will look similar to the screenshot below. Click Save in the toolbar to save your changes.