deviceTRUST 23.1.210
This service pack includes changes to the deviceTRUST Console, Agent and Client Extension for Microsoft Windows required to support the latest deviceTRUST Client Extension for iOS and iPadOS, in addition to other minor changes. Please refer to Compatibility for changes that may impact users upgrading from previous releases.
The deviceTRUST 23.1.202 patch includes a single bugfix to the deviceTRUST Agent.
The deviceTRUST 23.1.210 patch includes bugfixes to the deviceTRUST Console, Agent and Client Extension.
- Passcode authentication for iOS 17
- Minor enhancements to 23.1.200
- Bug fixes in 23.1.202
- Bug fixes in 23.1.210
- Compatibility
Passcode authentication for iOS 17
Previously when connecting to a virtual session with an iOS device, the deviceTRUST Agent matched the client name taken from the remoting protocol with the name of the registered iPhone or iPad within the deviceTRUST Portal. However with Apple’s continued push towards user privacy, the ability to query the name of the device is now limited to apps meeting specific criteria and requesting the necessary entitlement. Neither the deviceTRUST Client Extension for iOS, or any of the popular remoting clients, have been granted this entitlement. Having lost the only information we have that identifies the remote iOS device, a new approach to matching the remote device is required.
We now support the use of passcodes to match the remote device. When connecting from a remote iOS device, the deviceTRUST Agent will now display a passcode to the user of configurable length. The user must then switch to the deviceTRUST Client Extension for iOS and enter that passcode. They can then return to the virtual session to gain access to their desktop or published application.
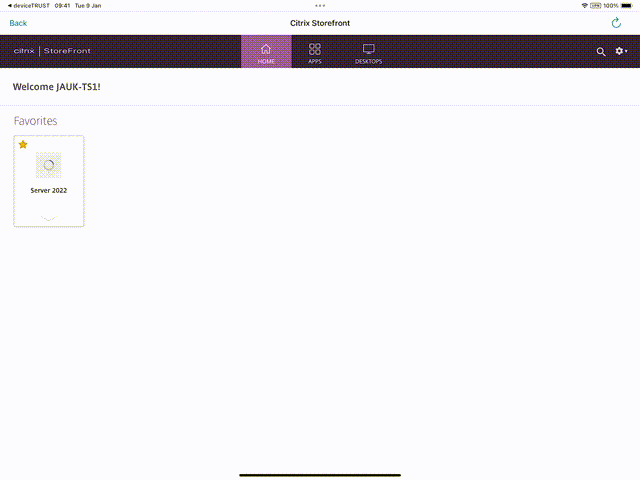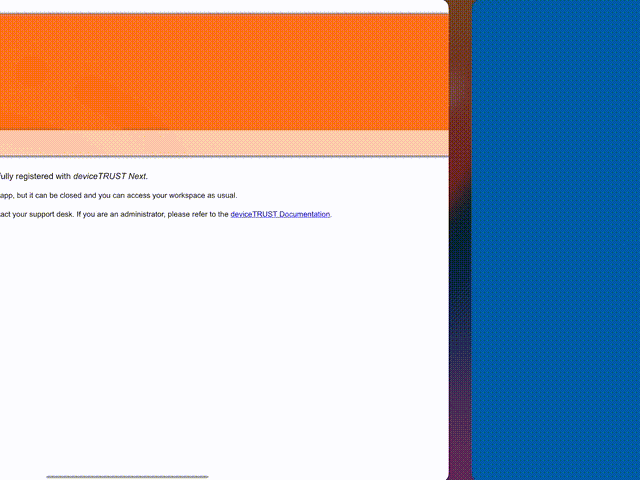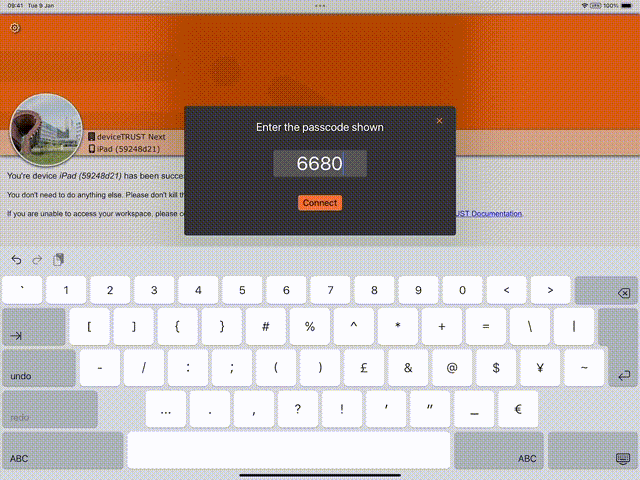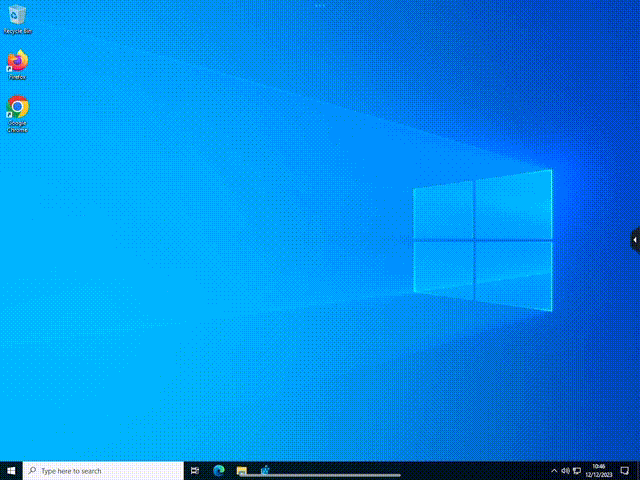
By using passcodes, we now support iOS as a remote device on Citrix Virtual Apps and Desktops, Citrix Cloud, Microsoft Remote Desktop Services and VMware Horizon View. For more information, see OS Compatibility.
More information can be found in the iOS Client Extension 23.1.200 release notes and iOS Passcodes reference.
Minor enhancements to 23.1.200
- Moved the mobile Server Url and Api Key from the ADMX templates into Mobile Settings.
- Added support for Location properties from iOS devices.
Bug fixes in 23.1.202
- Fixed an issue where the policy load would fail if Mobile Settings was not present within one of the loaded policies.
Bug fixes in 23.1.210
- Fixed an issue in both the deviceTRUST Client Extension and the deviceTRUST Agent where DCV connections would not be established due to the OS caching of data flowing over the DCV communications pipe.
- Fixed an issue in the deviceTRUST Agent where the clipboard could stop working following a reconnect to Citrix sessions running client OS’s.
- Fixed an issue in the deviceTRUST Console where the Location Properties could not be selected within context conditions when filtered for the iOS platform.
Compatibility
This compatibility section builds on our general approach to compatibility which can be found on the compatibility page.
If upgrading from a release prior to 23.1.120, be sure to check out the deviceTRUST 23.1.120 compatibility notes.
The new deviceTRUST Agent 23.1.200 remains compatible with previous deviceTRUST Client Extensions for iOS, however to use the new passcode authentication, both the agent and client extension must be using 23.1.200 or later.
The Group Policy Administrative Template ADMX/ADML files have been updated. If you previously used these to define a URL and Api Key to the deviceTRUST Portal, these will need moving into Mobile Settings.
The deviceTRUST Agents can read policies created by previous releases of the deviceTRUST Console. However, they cannot read policies created by a newer console. Therefore, you must ensure that the deviceTRUST Agent 23.1.200 is deployed before applying policy that has been written by the deviceTRUST Console 23.1.200 or later.
