deviceTRUST 20.2.100
This release includes new features and bug fixes to the deviceTRUST Console, Host and Client for Microsoft Windows. This includes significantly enhanced integration with Microsoft AppLocker and support for File-Based Policy. Please refer to Compatibility for changes that may impact users upgrading from previous releases.
- New Microsoft AppLocker Policy Settings
- File-Based Policy Settings
- Import and Export from Disk
- Updated Audit Event Task
- Environment variables
- Updates to deviceTRUST Command Line Processor
- Other changes
- Bug Fixes
- Known Limitations
- Compatibility
New Microsoft AppLocker Policy Settings
deviceTRUST 20.2 introduces a new Microsoft AppLocker Policy Settings page which allows configuration of the Microsoft AppLocker rules and settings. The functionality includes the creation of Executable, Windows Installer, Script and Packaged App rules. Each rule can be defined with path, file hashes or publisher conditions.
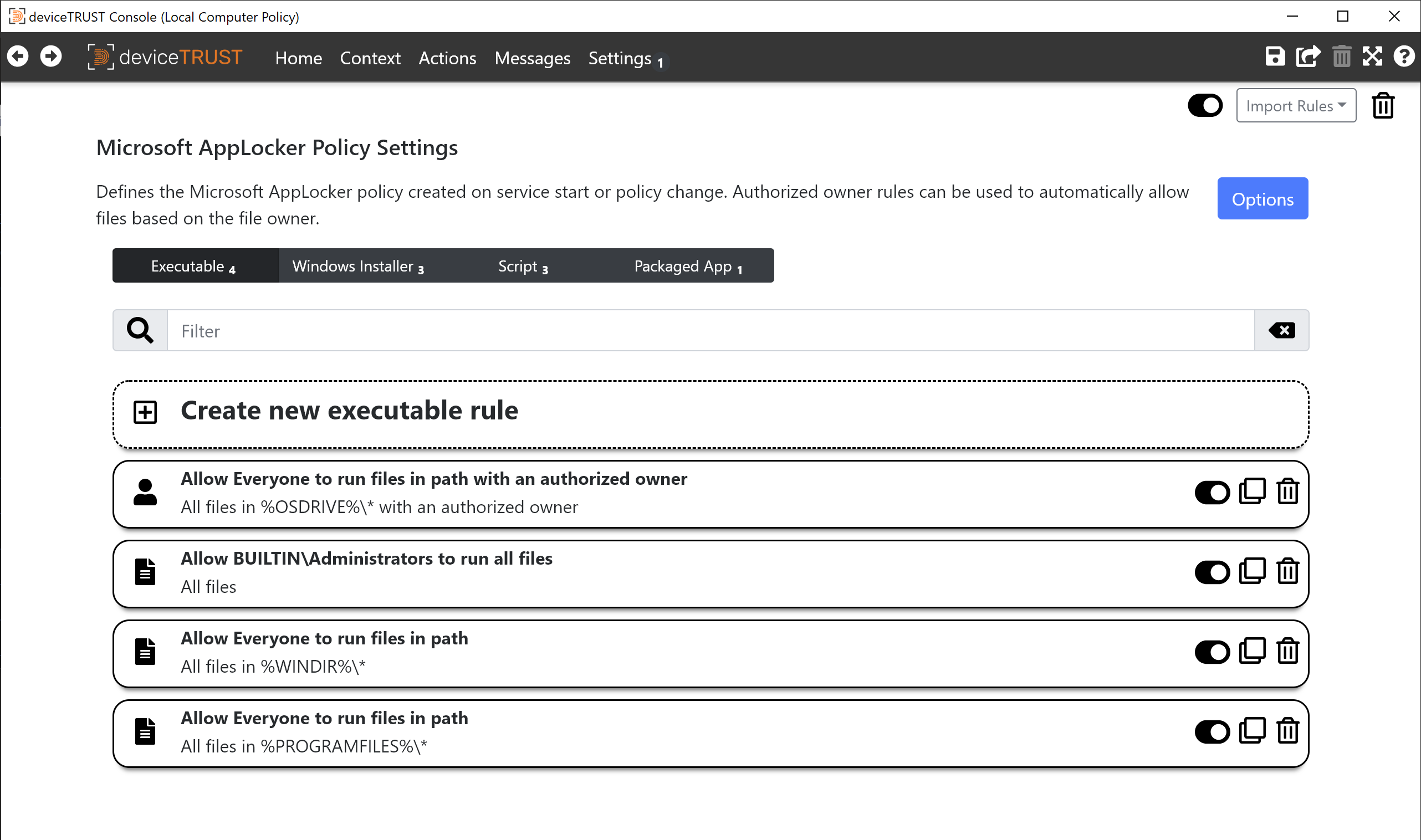
In addition to defining the rules applied to the local machine, you can also configure whether to start the Application Identity service, control the maximum file size of the AppLocker event logs, and change the enforcement rules for each rule collection.
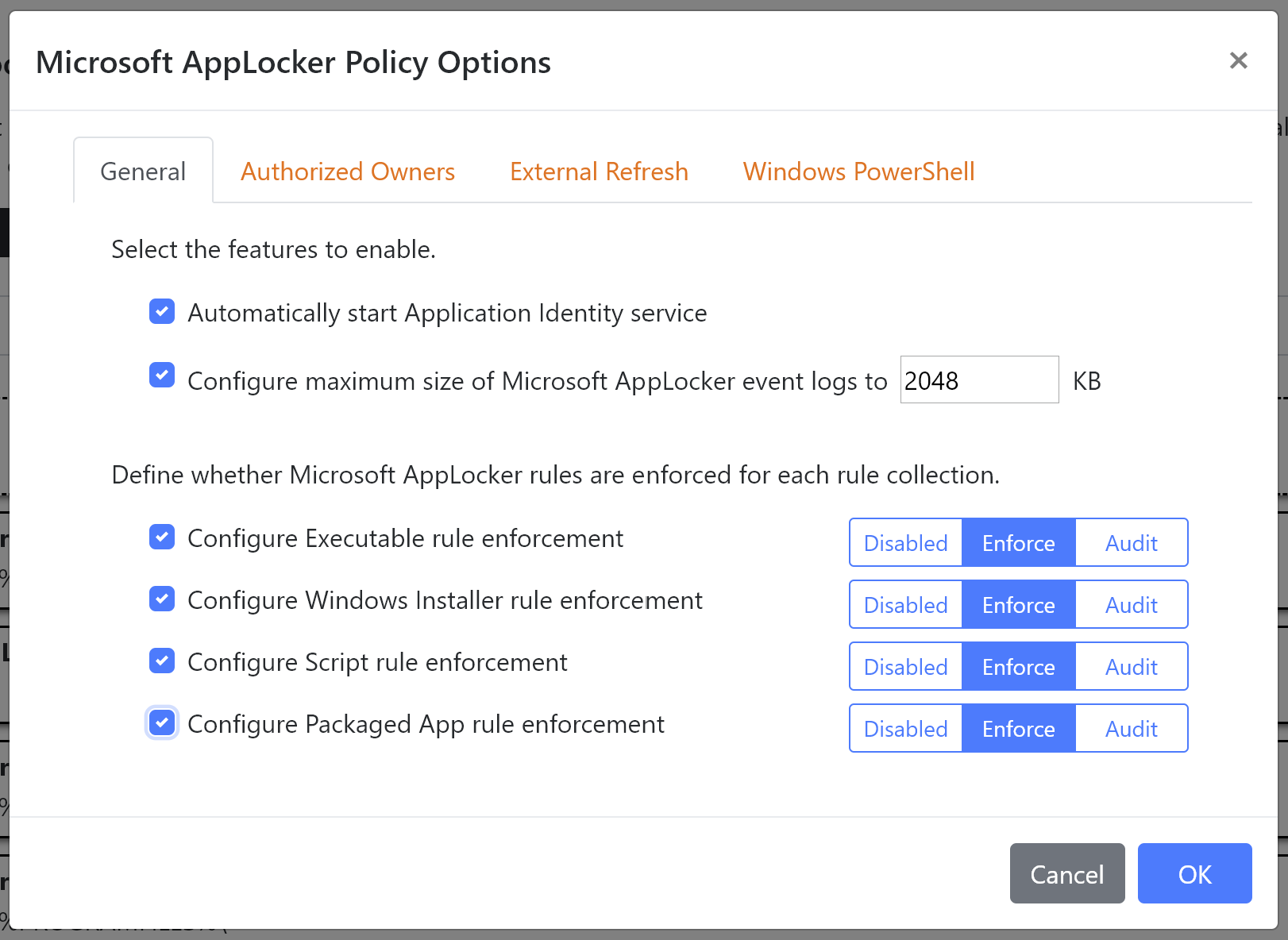
New Microsoft AppLocker Authorized Owner
We’ve introduced a new Authorized Owner rule type, which given a list of authorized owners will scan directories and sub-directories for Executables, Scripts and Windows Installers, looking for files which are owned by one of the authorized owners listed within the Authorized Owners tab of the Microsoft AppLocker Policy Options dialog.
When the above rule exists, the deviceTRUST Host will automatically generate rules such as in the following example:
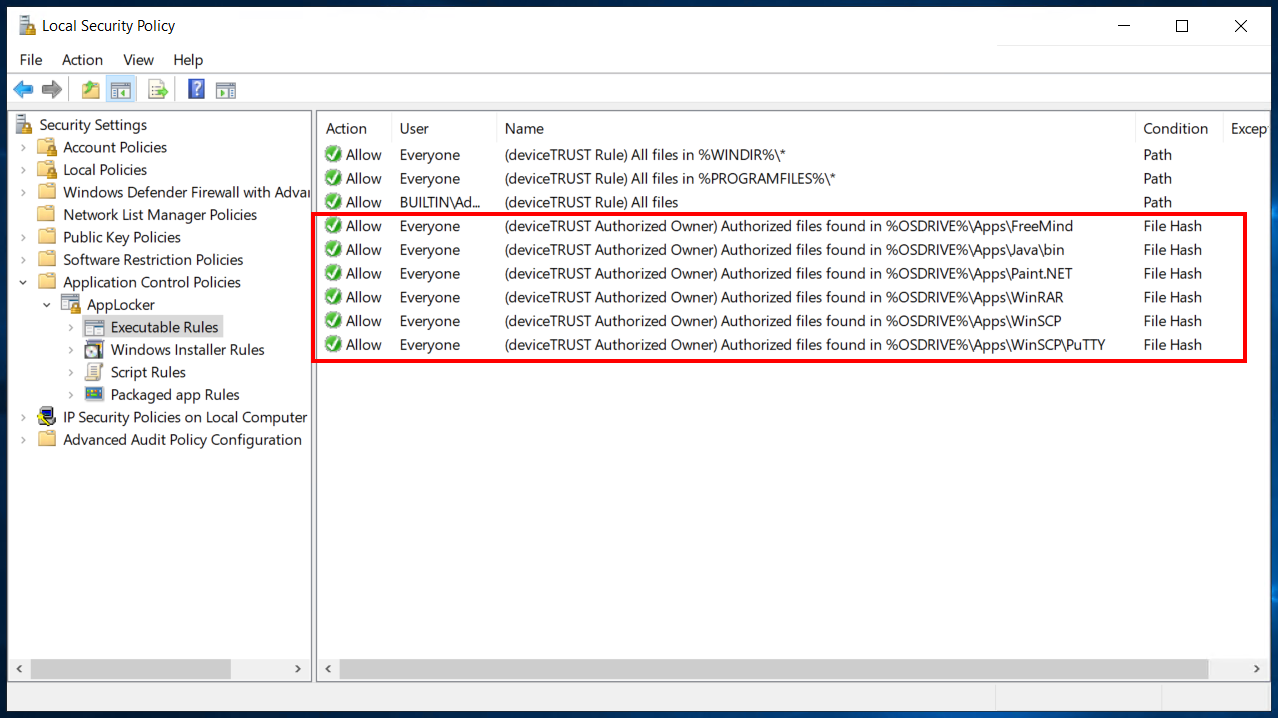
- The rules are automatically regenerated on computer startup, or whenever the policy changes.
- The rules can be regenerated by calling dtcmd APPLOCKER from an account specified within the External Refresh tab of the Microsoft AppLocker Policy Options. This enables a simple regeneration after deploying new application packages.
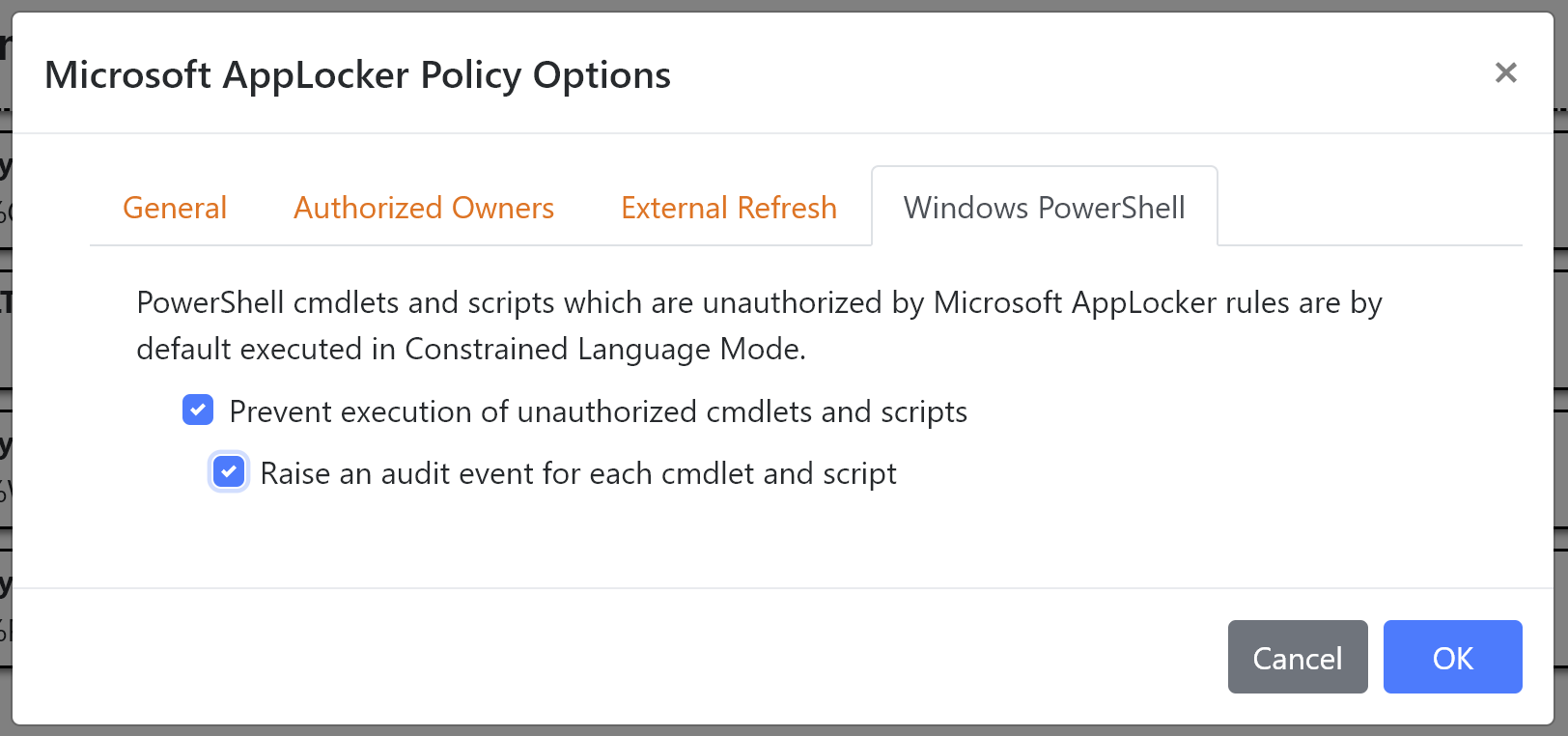
New control for Windows PowerShell Scripts and Cmdlets
On Windows Server 2016 and later, Windows PowerShell executes in a Constrained Language mode whenever the user is not authorized to run a PowerShell Script or Cmdlet. Constrained Language mode restricts access to sensitive language elements that can be used to invoke arbitrary Windows APIs.
deviceTRUST 20.2 includes a new option to entirely prevent execution of unauthorized PowerShell Scripts and Cmdlets. This ensures that only scripts permitted to execute according to the Microsoft AppLocker rules can execute.
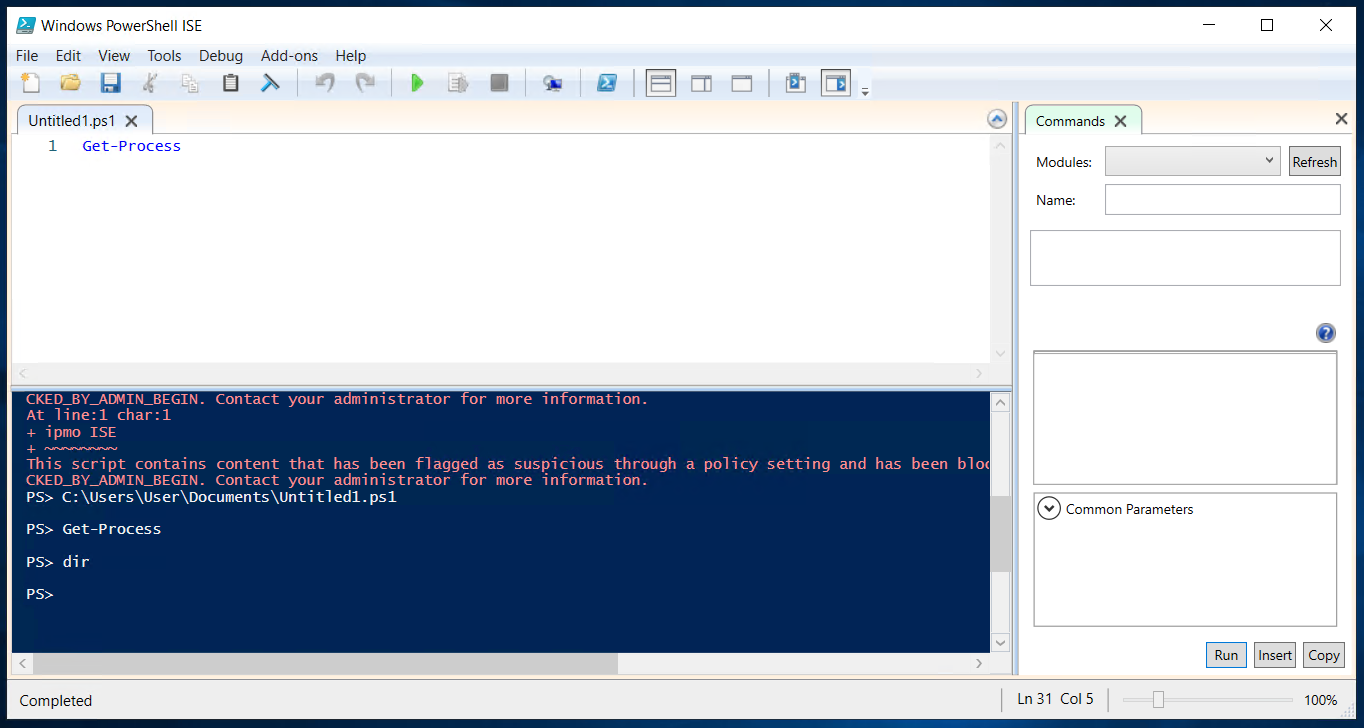
When denied by Microsoft AppLocker script rules, Windows PowerShell Scripts and Cmdlets fail to execute:
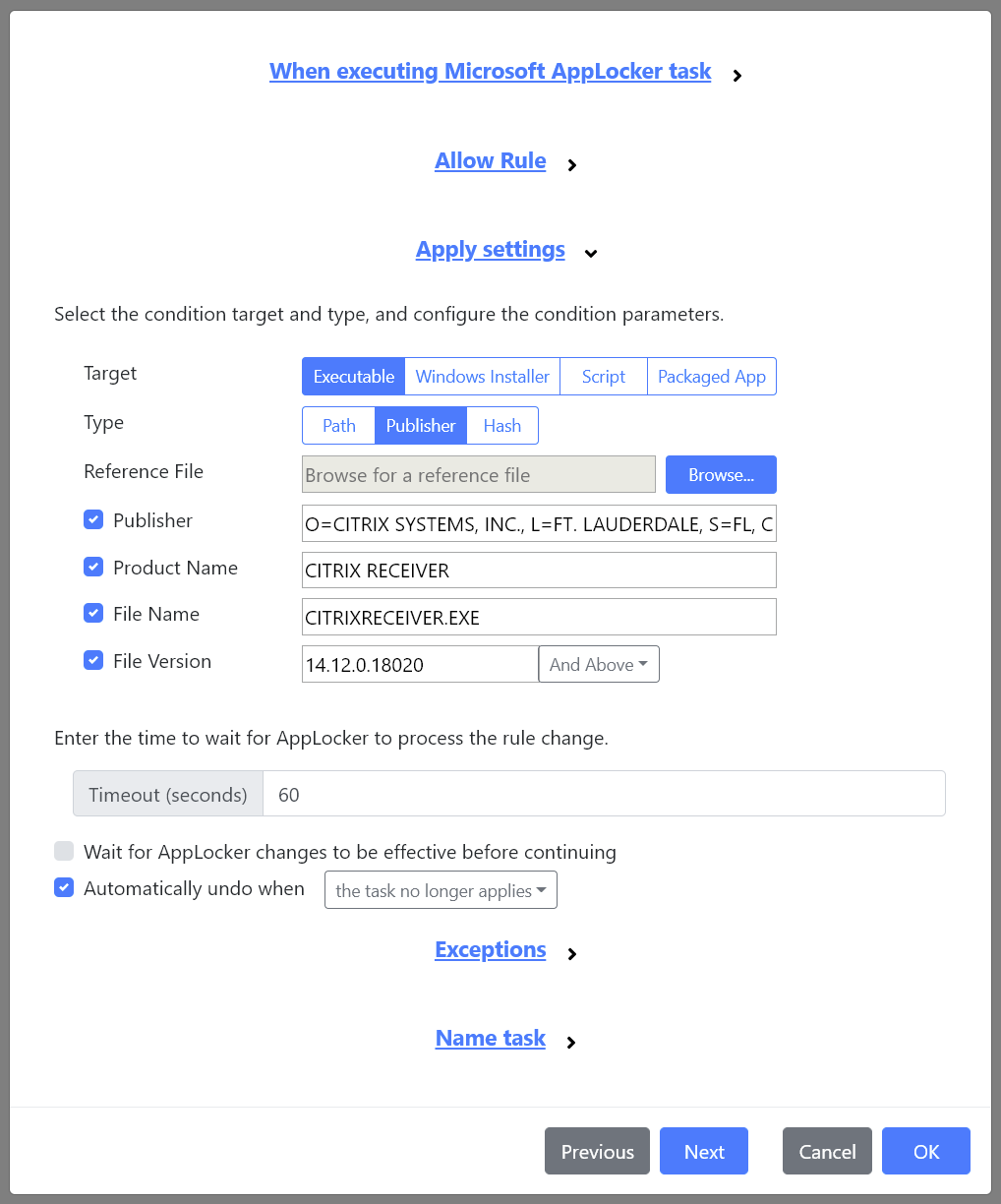
Updated Microsoft AppLocker Task
We’ve updated the Microsoft AppLocker task to match the functionality we’ve added to the Microsoft AppLocker Policy Settings. This includes path, file hash and publisher conditions, for Executable, Windows Installer, Script and Packaged App rules.
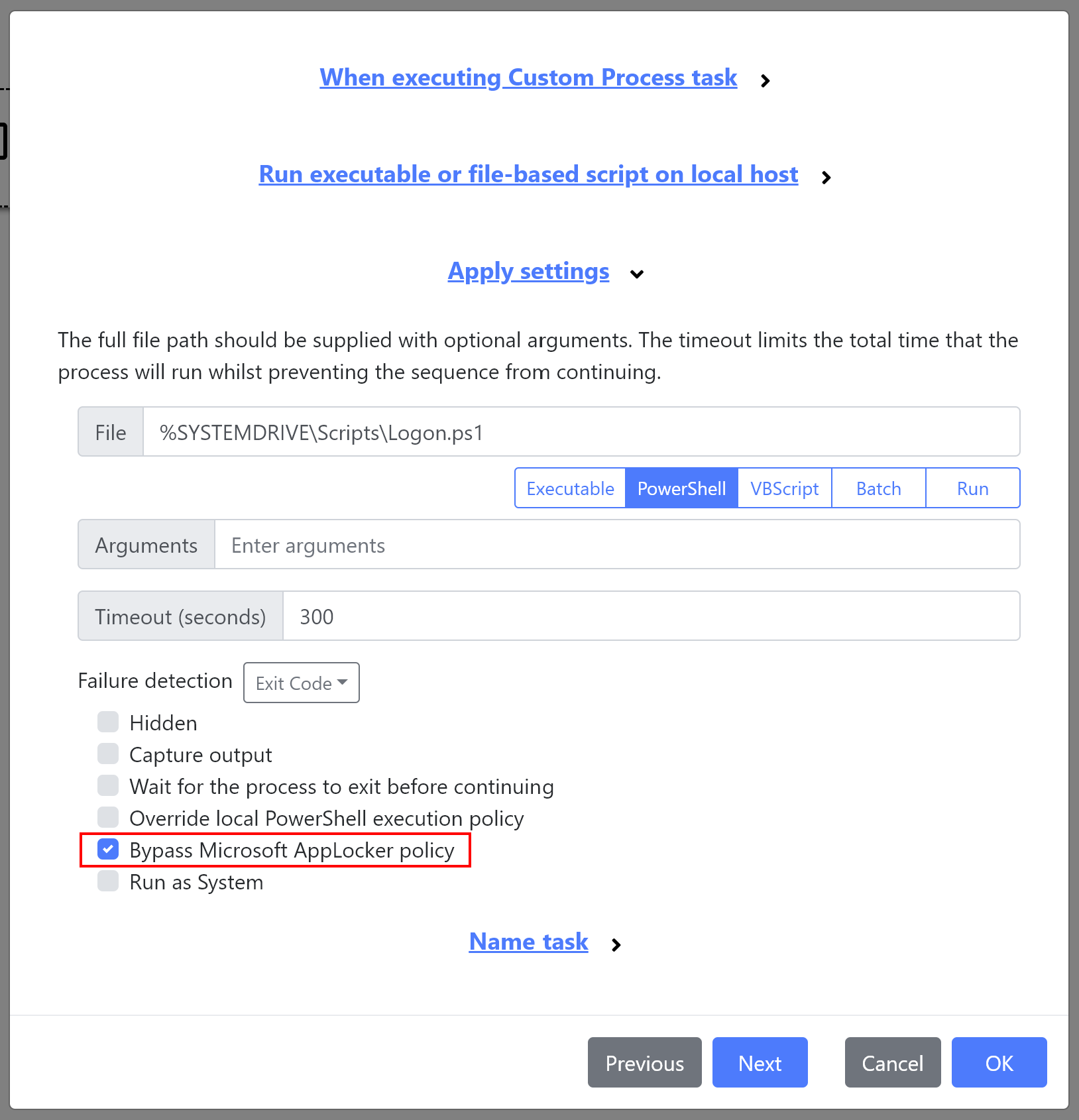
Custom Process Task and Microsoft AppLocker compatibility
To simplify the running of custom processes or scripts, we’ve introduced a new option to bypass Microsoft AppLocker policy within the Custom Process Task, and the Custom Properties Initalization Settings:
File-Based Policy Settings
deviceTRUST 20.2 now supports the loading of deviceTRUST policy files directly from disk, removing the requirement to use Group Policy.
The deviceTRUST Host now reads policy from Group Policy and then depending upon the File-Based Policy Settings, from the deviceTRUST policy folder located at %PROGRAMDATA%\deviceTRUST\Policy. Contexts, Actions, Messages and Settings are taken from group policy or the file with the highest priority. Priority is given first to Group Policy, and then to files in descending alphabetical order. For example, a context from policy_b.dtpol would override a similarly named context from policy_a.dtpol.
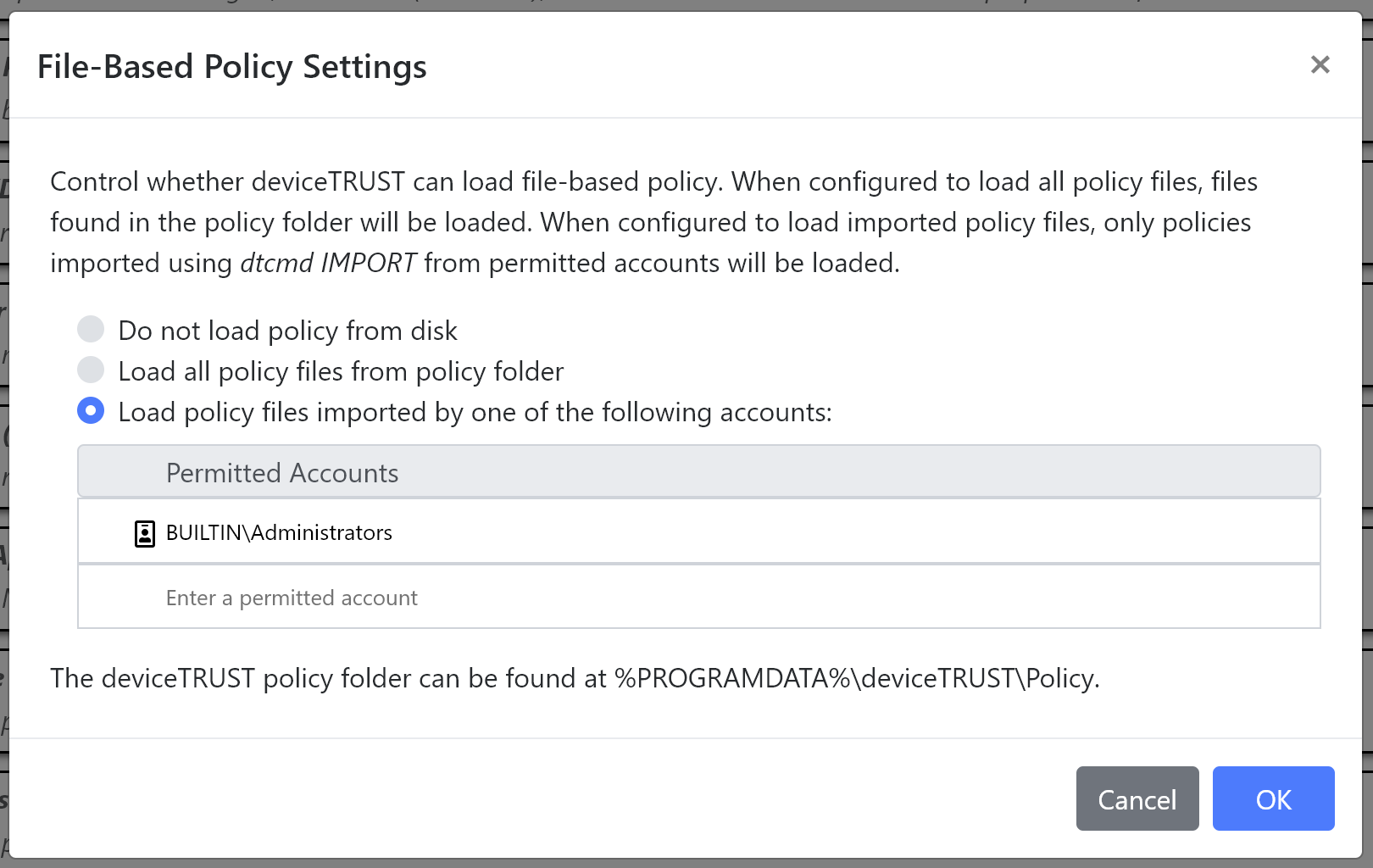
The File-Based Policy Settings provides the following control:
- Do not load policy from disk - The deviceTRUST Host does not attempt to load policy from the policy folder. Policy must be provided via Group Policy.
- Load all policy files from policy folder - Any file copied to the policy folder will be automatically loaded.
-
Load policy files imported by one of the following accounts - Ensures that the specified accounts can call
dtcmd IMPORTto import a policy file directly into the policy folder. All other files found within the deviceTRUST policy folder will be ignored.
- The deviceTRUST policy folder is located at `%PROGRAMDATA%\deviceTRUST\Policy`.
- The deviceTRUST Host will replace any local administrator ACL with read only access to the policy folder.
- deviceTRUST will continue to support deployment of policy from both Group Policy and File-Based Policy in the future.
Import and Export from Disk
We’ve extended our sharing options with three new options aimed at simplifying working with files on disk.
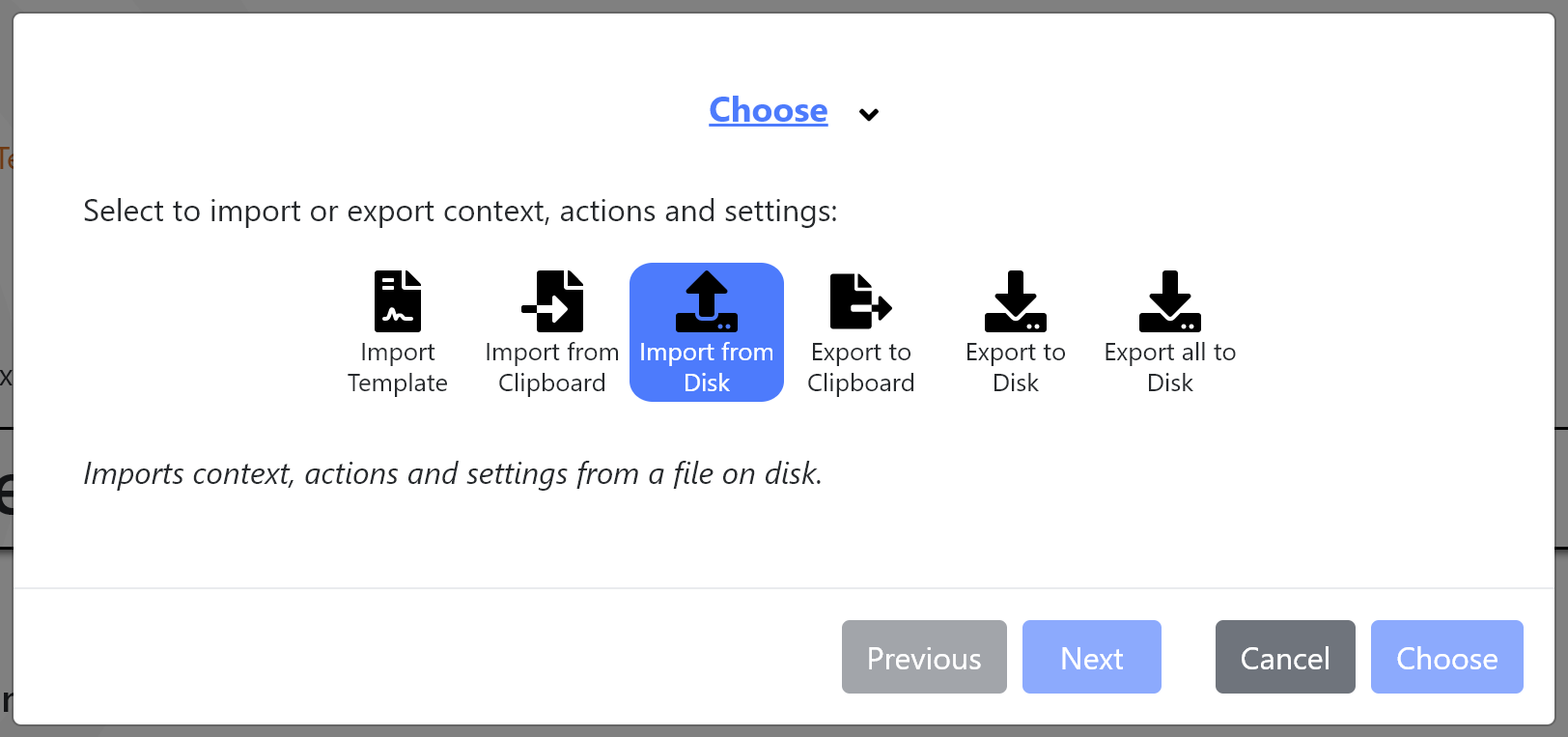
- Import from Disk - Imports a selection of Contexts, Actions, Messages and Settings from a deviceTRUST Policy (*.dtpol) file.
- Export to Disk - Exports a selection of Contexts, Actions, Messages and Settings to a deviceTRUST Policy (*.dtpol) file.
- Export all to Disk - Exports all Contexts, Actions, Messages and Settings to a deviceTRUST Policy (*.dtpol) file.
Updated Audit Event Task
The Audit Event task has been extended with two new options aimed at simplifying integration with SIEM solutions.
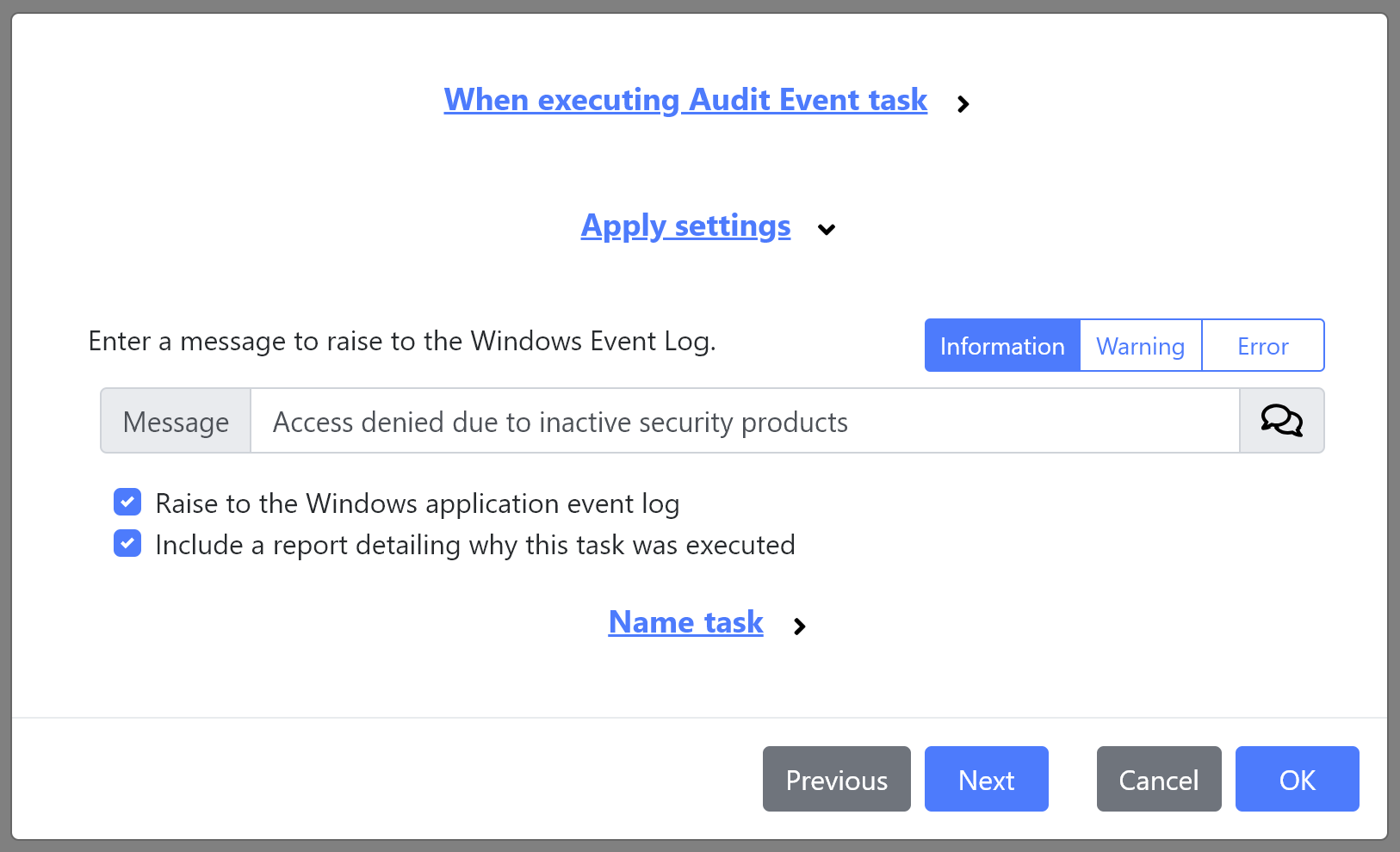
When Raise to the Windows application event log is checked, the deviceTRUST Host will raise the audit event to Windows Logs -> Application.
When Include a report detailing why this task was executed is checked, the deviceTRUST Host will include the following meta-data with the event:
- ReportTrigger - The trigger that resulted in the task being executed, such as Logon or ContextChanged.
- ReportAction - The name of the action that generated the event.
- ReportDeviceName - The name of the remote device that the user was connecting from.
- ReportDeviceOSName - The OS name of the remote device that the user was connecting from.
- ReportDeviceOSType - The OS type, such as Client or Server that the user was connecting from.
- ReportClientVersion - The version of the deviceTRUST Client that was used to establish the remote device information.
- ReportContexts - The name and value of all contexts.
- ReportProperties - The name and value of all properties.
The Persistence setting can be used to limit the properties that are included within the audit event to protect a users privacy.
Environment variables
Text input fields within the deviceTRUST Console now accept environment variables which are evaluated by the deviceTRUST Host when the policy is loaded. Text input fields accept the following variables:
- Environment variables from the user or system, such as %USERNAME% or %USERDOMAIN%.
- The variable %SYSTEMDOMAIN% for referencing the domain that the local machine is joined.
- References to deviceTRUST HOST, DEVICE or MULTIHOP properties such as %HOST_OS_VERSION%.
- References to deviceTRUST CONTEXT properties, such as %CONTEXT_SECURITY_STATE%.
- References to deviceTRUST messages, such as %MESSAGE_TITLE%.
Updates to deviceTRUST Command Line Processor
We’ve removed legacy options from dtcmd, including ACCESS, APPLOCKER, APPTERMINATE, EVENT and POPUP. If you currently use these, then see Compatibility for alternative options.
The exit codes have also been standardized across all options. Calls to dtcmd now return:
- Success (0)
- Permission Denied (1)
- File Not Found (2)
- Other Error (3)
Other changes
- The default timeout period where security products will read from the cache whenever a Windows Security Center reports no security products has increased from 10 minutes to 30 minutes after computer startup.
Bug Fixes
- Fixed an issue where HOST_LOCATION_COUNTRY and DEVICE_LOCATION_COUNTRY could be set to the value “-9” when accessing from France, Norway or Cyprus.
- Fixed an issue where the caching of security products could fail, resulting in no security products reported shortly after computer startup.
Known Limitations
- Changes to Microsoft AppLocker policy requires that Local Policy has not been disabled within Group Policy, and that the machine has connectivity with the domain controller.
- Care should be taken when using Local Policy to edit Microsoft AppLocker Policy settings. This includes when using the deviceTRUST Console, or the Local Group Policy Editor. Since both of these editors load a snapshot of the Local Policy, which includes the Microsoft AppLocker rules, saving the policy will overwrite the Microsoft AppLocker rules with the rules from when the editor was first launched.
- We’ve seen problems on Windows 10 2004 and 20H2 where timestamps displayed in Event Viewer are shown within the General tab as ‘1601-01-01’. This specifically impacts our licensing events with ID 11 to 16. To work around this issue, the correct values can be seen by clicking on the Details tab of the same event.
Compatibility
If upgrading from deviceTRUST 19.4 or earlier, be sure to refer to the deviceTRUST 20.1.100 Compatibility notes.
If upgrading from deviceTRUST 20.1.200 or earlier, be sure to refer to the deviceTRUST 20.1.300 Compatibility notes.
We’ve removed dtcmd ACCESS, APPLOCKER, APPTERMINATE, EVENT and POPUP. If you are using any of these options, then you will need to create a named trigger within an action, create a suitable task to replace the call, and invoke the named trigger using dtcmd TRIGGER /action:<nameofaction> /name:<nameofsequence>.
The ADMX policy definitions contain cosmetic changes, the removal of the security policies required to support dtcmd and also control for enabling or disabling some new auditing events. If you are already using ADMX policy definitions from 20.1.100 or later these will continue to work with 20.2.
The 20.2.100 client contains only Bug Fixes over the 20.1.300 client. If these issues are unlikely to impact you, then the 20.1.300 client will continue to work with the deviceTRUST 20.2.100 Host.
